The most secure browser for transmitting sensitive data is definitely not Chrome

Jack Wallen addresses the challenging question of which browser is best to use for transmitting encrypted data.
Image: Yuichiro Chino/Moment/Getty Images
TL:DR: Tor.
Yep, that’s the answer. The most secure browser for encrypted data is Tor. But there’s a catch… and it’s a big one. You might work within a company LAN that doesn’t allow for the Tor browser to function. And unless you can get your IT department to open up the network to allow Tor to function, you’re out of luck.
But for everyone else, Tor is definitely the browser to beat when it comes to encrypted transmitted data.
SEE: Security incident response policy (TechRepublic Premium)
Let me offer up a simple example.
Once upon a time, I was hired by a new client. Now, this client didn’t exactly engender much in the way of trust in me, but they were willing to pay a premium for me to generate content for them. But lodged in the back of my mind was this sense I couldn’t trust them 100%. So, what did I do? I created a virtual network, detached from my primary network and then deployed a virtual machine attached to that network. On that virtual machine (running Ubuntu Desktop), I installed the Tor browser. With that setup, I felt absolutely confident nothing untoward could happen… unless I was dealing with serious hackers.
I keep the Tor browser installed on my desktops and laptops on the off chance I need to transmit sensitive data that goes well beyond the standard. Or, if I’m on the go and can’t exactly trust the network I’m using, I immediately fire up Tor and have at my work.
But what do you do when Tor isn’t an option? Toss your hands in the air (like you just don’t care) as if to say, “Let’s just hand over all of my sensitive data to anyone who wants to view it!”? No, you don’t have to do that.
Now, to be clear, we’re not talking about privacy, as that’s another matter altogether. We’re talking about sending encrypted data. For that, where do you turn?
You might think Brave is the answer. After all, Brave is the browser focused primarily on privacy. But, again, we’re not talking about privacy. And given that Brave includes features centered around cryptocurrency, and although I wouldn’t call out Brave for crypto mining, there is no certainty when it comes to that technology. But the primary reason I leave Brave out of this is because its primary security functionality is centered on privacy.
For me, the nod for encrypted data when Tor isn’t an option goes to Firefox. Why? Outside of third-party add-ons you can install for even more protection, Firefox includes an HTTPS-only mode out of the box. Although it’s not enabled by default, you can go to Settings | Privacy & Security and enable HTTPS-only mode (Figure A), which will force an encrypted connection between your machine and the sites you visit.
Figure A
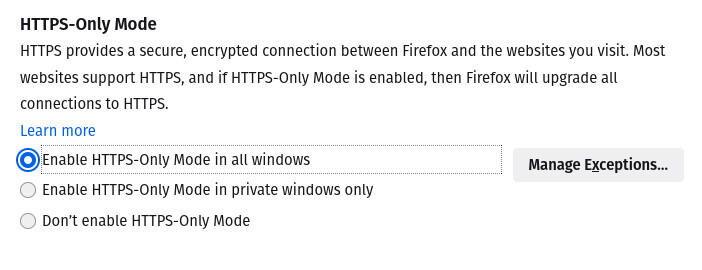
Enabling HTTPS-only mode in Firefox.
This mode could break some sites you use. Fortunately, the developers made it possible for you to add exceptions to the rule. But enabling this feature will always ensure your connections are made over the more secure HTTPS.
That, of course, isn’t the only reason Firefox gets the nod. The browser’s Enhanced Tracking Protection makes it possible for you to completely block all tracking from sites, either globally or on the fly. So when I’m about to transmit sensitive data, I’ll open Firefox, clear my history, set Enhanced Tracking Protection to Strict, and then do what I need to do. When I’m done, I reset Enhanced Tracking Protection to Standard and continue with my day. I leave HTTPS-only mode on at all times.
This is all based on my own personal experience. For me, the browser I always reach for when dealing with very sensitive data is Tor. When Tor isn’t an option, I go with Firefox. It really is that simple.
What about you? What browser is at the top of your list of must-use for security purposes?
Subscribe to TechRepublic’s How To Make Tech Work on YouTube for all the latest tech advice for business pros from Jack Wallen.


