- UK Government Publishes Plan to Boost Cyber Sector Growth
- This LG C4 OLED TV is over 50% off on Amazon right now - and I highly recommend it
- 4 PC parts I'm buying to upgrade my computer (and the 7 I'm keeping)
- 8 steps to ensure data privacy compliance across borders
- My 6 favorite open-source Android apps from the Google Play store - and why that matters
The Scam Strikes Back: Exploiting the CrowdStrike Outage | McAfee Blog

Authored by Lakshya Mathur, Vallabh Chole & Abhishek Karnik
Recently we witnessed one of the most significant IT disruptions in history, affecting a wide range of sectors such as banking, airlines, and emergency services. At the heart of this disruption was CrowdStrike, known for its Falcon enterprise security solutions. The issue stemmed from a faulty security update that corrupted the Windows OS kernel, leading to a widespread Blue Screen of Death (BSOD).
The incident spurred opportunistic behaviors among scammers and malware creators. McAfee Labs noted:
- Non-Delivery Scams: Early signs of potential non-delivery scams shortly after the event, with some online stores quickly marketing merchandise that mocked the CrowdStrike incident.
- Domain Spoofing: A noticeable surge in domain registrations containing the term “CrowdStrike” following the onset of the outage, there was Scammers may register domain names to trick people into thinking the site is related to a legitimate or familiar company, to deceive users into visiting the site for phishing attacks, spreading malware, or collecting sensitive information.
- Malware: Malware developers swiftly disguised harmful software like Remcos, Wiper, and Stealers as remediation tools for the outage. Unsuspecting people may have downloaded this software in an effort to restore their systems.
Voice Scams: There were also reports of robocalls offering assistance for these issues, though these claims have not been verified by McAfee.
It’s important to note that Mac and Linux users were unaffected by this incident, as the problems were confined to Windows systems. Furthermore, since CrowdStrike primarily serves the enterprise market, the crashes predominantly affected business services rather than personal consumer systems. However, the ripple effects of the disruption may have caused inconvenience for consumers dealing with affected service providers, and all consumers should be extra vigilant regarding unsolicited communications from sources claiming to be an impacted business.
This blog outlines the various malware threats and scams observed since the outage occurred on Friday, July 19, 2024.
CrowdStrike Themed Malware
- Stealer payload via doc-based Macros
This file, which seems to provide recovery guidelines, covertly incorporates a macro that silently installs malware designed to steal information.
Malicious doc first page
Infection Chain
Zip -> Doc -> Cmd.exe -> Curl.exe -> Malicious URL -> Rundll32.exe -> Infostealer DLL payload
Doc file uses malicious macros, Curl.exe and Certutil.exe to download malicious infostealer DLL payload.
The stealer terminates all running Browser processes and then tries to steal login data and coolies from different browsers. All the stolen data is saved under %Temp% folder in a text file. This data is sent to the attacker’s C2 server.
- PDF file downloading Wiper Malware
Attackers use a PDF file and malicious spam to trick victims into downloading a supposed recovery tool. Clicking the provided link connects to a malicious URL, which then downloads a Wiper malware payload. This data wiper is extracted under %Temp% folder and its main purpose is to destroy data stored on the victim’s device.
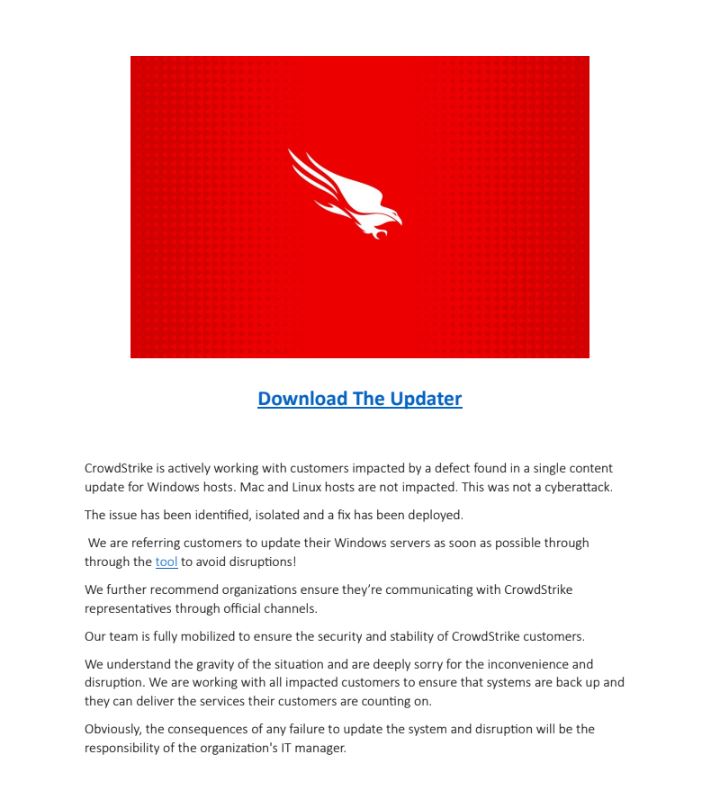
PDF file with CrowdStrike remediation tool theme
Infection Chain
PDF -> Malicious URL -> Zip -> Wiper payload
- Remcos RAT delivered with CrowdStrike Fix theme
Zip files labeled “crowdstrike-hotfix.zip” that carry Hijack Loader malware, which then deploys Remcos RAT, have been observed being distributed to victims. Additionally, the zip file includes a text file with instructions on how to execute the .exe file to resolve the issue.
Remcos RAT allows attackers to take remote access to the victim’s machine and steal sensitive information from their system.
CrowdStrike Outage Impersonated Domains & URLs
Once the outage gained media attention, numerous domains containing the word “crowdstrike” were registered, aimed at manipulating search engine results. Over the weekend, several of these newly registered domains became active.
Here are some examples:
https[:]//pay.crowdstrikerecovery[.]com/ , pay[.]clown-strike[.]com , pay[.]strikeralliance[.]com
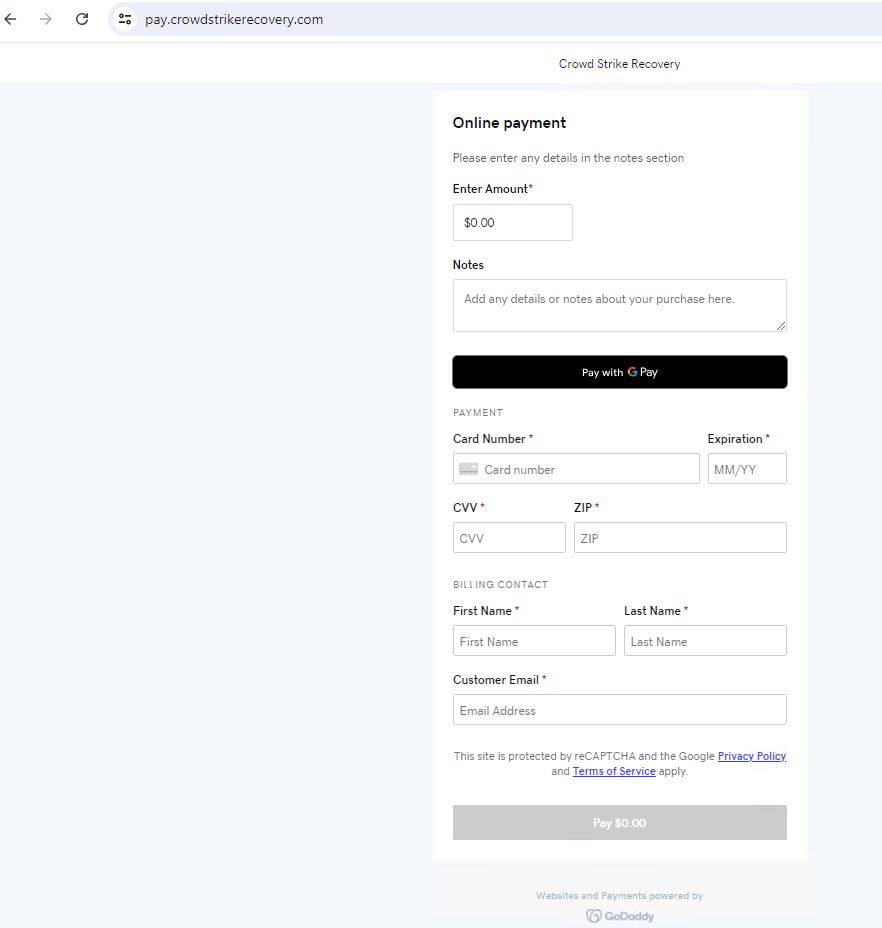
The rogue domains lead to the payments page
Crowdstrike-helpdesk[.]com
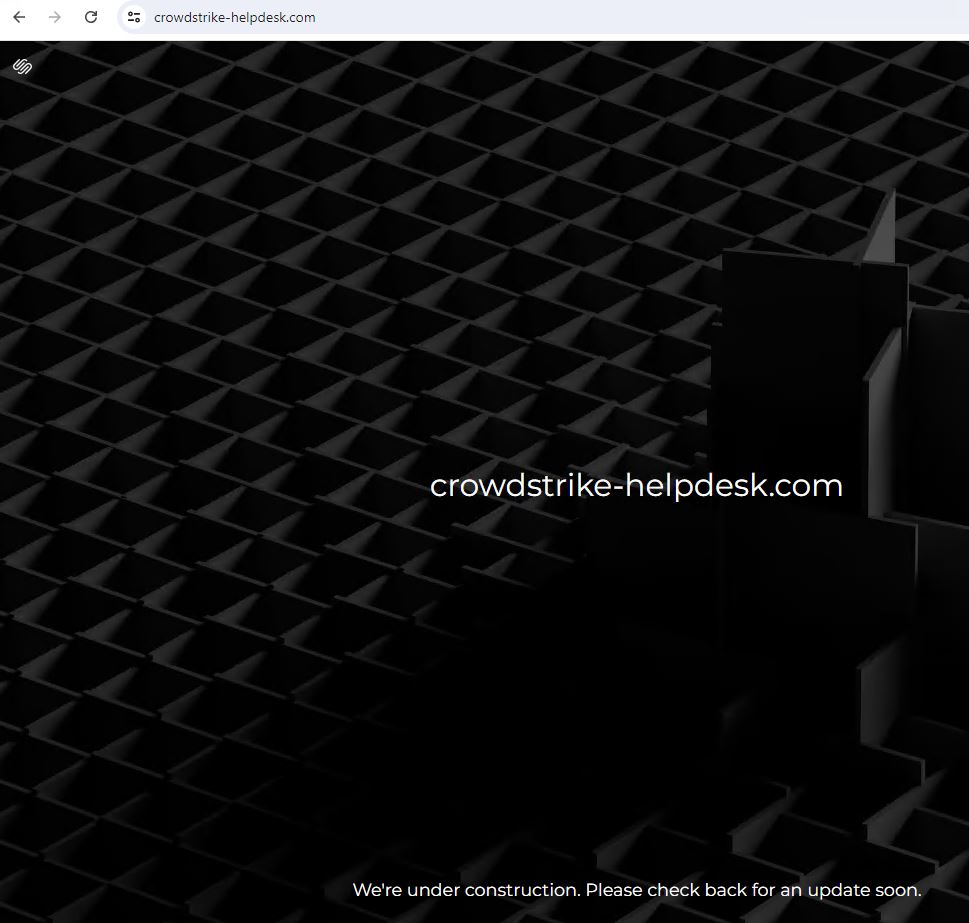
Domains that are currently parked and not live
- Additionally, numerous cryptocurrency wallets were established using a theme inspired by CrowdStrike.
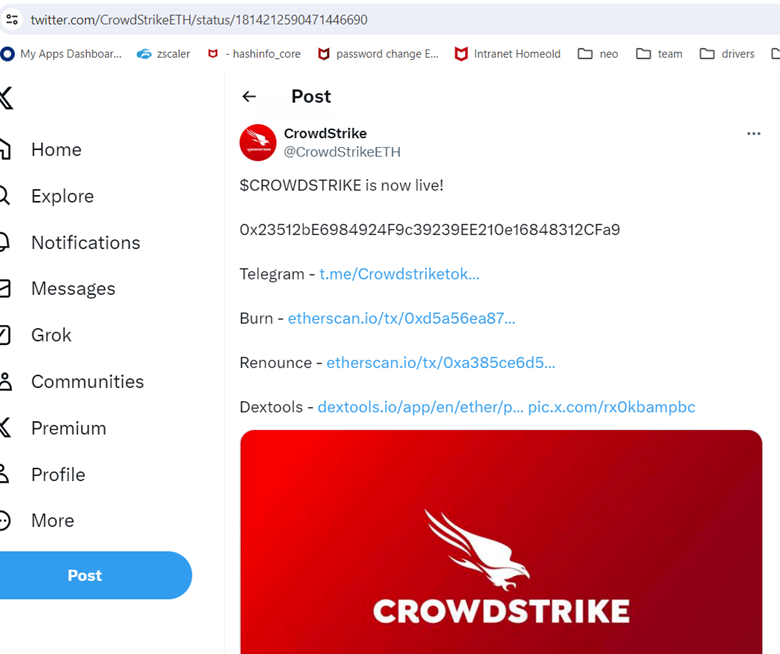
twitter[.]com/CrowdStrikeETH/
Some other wallets related to CrowdStrike Outage apart from above mentioned.
bitcoin:1M8jsPNgELuoXXXXXXXXXXXyDNvaxXLsoT
ethereum:0x1AEAe8c6XXXXXXXXXXX76ac49bb3816A4eB4455b
To summarize, the majority of consumers using devices at home might not be directly affected by this incident. However, if you have experienced issues such as airline delays, banking disruptions, healthcare, or similar service interruptions since July 19th, they could be related to this event.
Be wary if you receive phone calls, SMS messages, emails, or any form of contact offering assistance to remedy this situation. Unless you operate a business that uses CrowdStrike, you are likely not affected.
For the remediation process and steps follow the official article from CrowdStrike – https://www.crowdstrike.com/falcon-content-update-remediation-and-guidance-hub/
List of known malware hashes and potentially unwanted domains:
| Hashes | Type |
| 96dec6e07229201a02f538310815c695cf6147c548ff1c6a0def2fe38f3dcbc8 | Wiper Zip |
| 803727ccdf441e49096f3fd48107a5fe55c56c080f46773cd649c9e55ec1be61 | Stealer Docx |
| c44506fe6e1ede5a104008755abf5b6ace51f1a84ad656a2dccc7f2c39c0eca2 | RemcosRAT Zip |
| 19001dd441e50233d7f0addb4fcd405a70ac3d5e310ff20b331d6f1a29c634f0 | Wiper PDF |
| d6d5ff8e9dc6d2b195a6715280c2f1ba471048a7ce68d256040672b801fda0ea | RemcosRAT DLL |
| 4491901eff338ab52c85a77a3fbd3ce80fda738046ee3b7da7be468da5b331a3 | Wiper EXE |
| Domains |
| hxxps://crowdstrike0day[.]com |
| hxxps://crowdstrikefix[.]com |
| hxxps://crowdstrike-bsod[.]com |
| hxxps://crowdstrikedoomsday[.]com |
| hxxps://crowdstrikedown[.]site |
| hxxps://www[.]crowdstriketoken[.]com |
| hxxps://crowdstriketoken[.]com |
| hxxps://crowdstrikebsod[.]com |
| hxxps://fix-crowdstrike-apocalypse[.]com |
| hxxp://crowdfalcon-immed-update[.]com |
| hxxp://crowdstrikefix[.]com |
| hxxp://fix-crowdstrike-apocalypse[.]com |
| hxxps://crowdstrike[.]phpartners[.]org |
| hxxps://www[.]crowdstrikefix[.]com |
| hxxp://crowdstrikebsod[.]com |
| hxxp://crowdstrikeclaim[.]com |
| hxxp://crowdstrikeupdate[.]com |
| hxxp://crowdstrike[.]buzz |
| hxxp://crowdstrike0day[.]com |
| hxxp://crowdstrike-bsod[.]com |
| hxxp://crowdstrikedoomsday[.]com |
| hxxp://crowdstrikedown[.]site |
| hxxp://crowdstrikefix[.]zip |
| hxxp://crowdstrike-helpdesk[.]com |
| hxxp://crowdstrikeoutage[.]info |
| hxxp://crowdstrikereport[.]com |
| hxxp://crowdstriketoken[.]com |
| hxxp://crowdstuck[.]org |
| hxxp://fix-crowdstrike-bsod[.]com |
| hxxp://microsoftcrowdstrike[.]com |
| hxxp://microsoftcrowdstrike[.]com/ |
| hxxp://whatiscrowdstrike[.]com |
| hxxp://www[.]crowdstrikefix[.]com |


