- The iPad I recommend to most users is only $299 right now
- One of the most versatile action cameras I've tested isn't from GoPro - and it's on sale
- Small Manufacturers, Big Target: The Growing Cyber Threat and How to Defend Against It
- Why I pick this JBL speaker over competing models for outdoor listening
- Testing a smart cooler proved I can never go back to toting ice (and it's on sale)
This Android malware lures in victims with fake vaccine appointments
Attempting to keep track of every form of malware targeting Android devices has become virtually impossible. Earlier this year, we wrote about the dangers of FluBot. Cyber threat actors are sending text messages to Android users informing them that they’ve missed a package. If that user clicks on the link in the text message, it will prompt them to download a phishing app. FluBot’s still spreading, but now researchers have uncovered a new Android malware known as TangleBot.
Beware of the TangleBot Android malware
Late last month, Cloudmark threat analysts reported on a “clever and complicated new SMS malware attack.” Just like FluBot, TangleBot uses text messages to trick people into clicking on malicious links. The biggest difference appears to be the contents of those messages.
Rather than fool users into thinking that they missed a delivery, TangleBot uses COVID-19 as a cover for the scam. Some messages tell users to click a link to see new COVID-19 regulations in their area. Other messages try to convince users that they’ve received an appointment for the third dose of a vaccine. It’s a ruthless and disgusting tactic, but admittedly a very clever one.
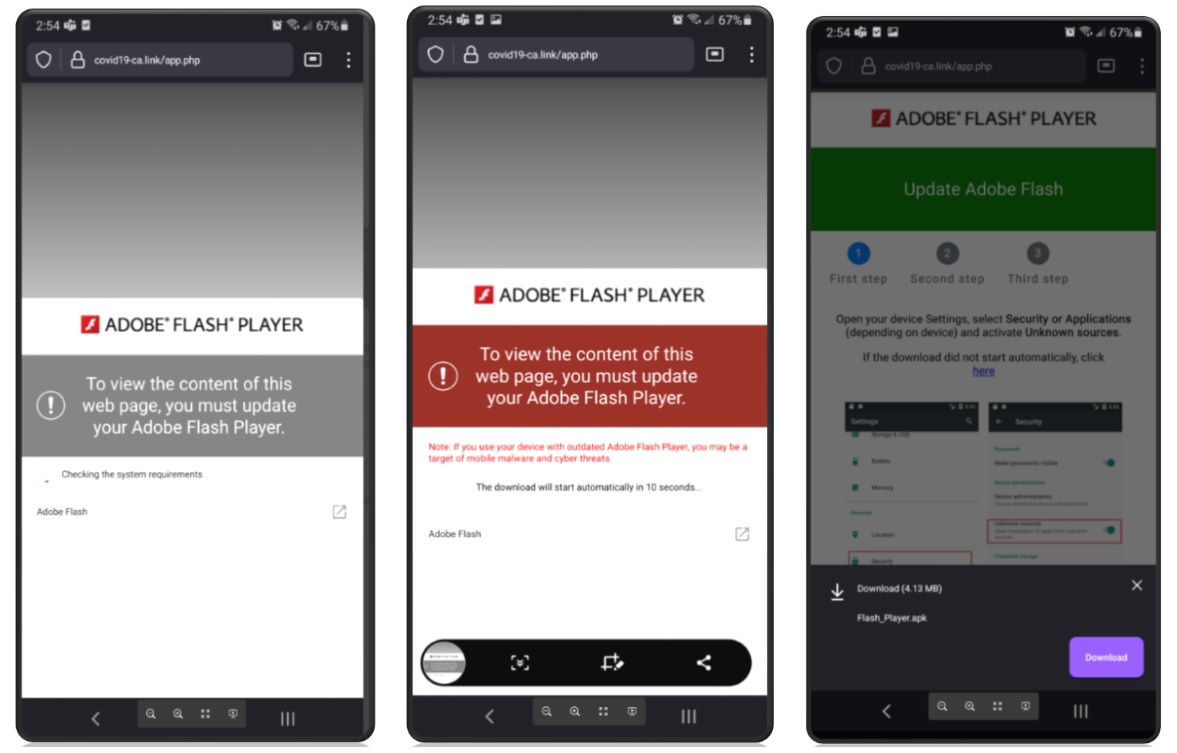
If an Android device owner falls into the trap and clicks the malicious link, the consequences can be dire. After clicking the link, the user sees a website warning them Adobe Flash Player on the device is out of date. The site then offers them the choice to update Flash Player. If the user clicks through the resulting dialog boxes, they will install the TangleBot malware on their device.
Here’s how dangerous the malware can be
Once TangleBot is installed on an Android phone or tablet, it can gain access to that device’s contacts, text and call capabilities, call logs, internet, camera, microphone, and GPS. According to Cloudmark’s threat analysts, attackers can then do the following with the user’s device:
- make and block phone calls
- send, obtain, and process text messages
- record the camera, screen, or microphone audio or stream them directly to the attacker
- place overlay screens on the device covering legitimate apps and screens
- implement other device observation capabilities
If you fall for this trick, attackers could steal your accounts, harass your contacts, and make your life miserable. These SMS scams aren’t going anywhere, as they are among the most effective ways to target millions of potential victims all at once. Protect yourself by staying alert at all times. Don’t take calls, click on links, or open emails from anyone other than the people you trust.
If you want to know more about TangleBot, check out this detailed breakdown from Proofpoint.

