- Your iPad is getting a major upgrade for free. 4 top features I can't wait to try in iPadOS 26
- Your MacBook is getting a big upgrade. 5 best features I can't wait to use in MacOS 26
- The Growing Threat of AI-powered Cyberattacks in 2025
- I test tablets for a living and this is the Samsung tablet I recommend the most
- The Cost of Ignoring Patches: How State and Local Governments Can Mitigate Damaging Security Breaches
US DoJ indicts four members of China-linked APT40 cyberespionage group
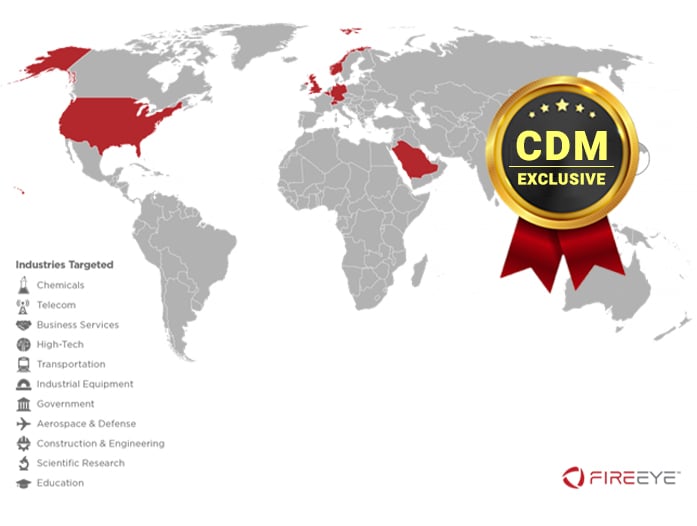
US DoJ indicted four members of the China-linked cyberespionage group known as APT40 for hacking various entities between 2011 and 2018.
The U.S. Justice Department (DoJ) indicted four members of the China-linked cyber espionage group APT40 (aka TEMP.Periscope, TEMP.Jumper, and Leviathan) for hacking tens of government organizations, private businesses and universities around the world between 2011 and 2018.
“The defendants and their Hainan State Security Department (HSSD) conspirators sought to obfuscate the Chinese government’s role in such theft by establishing a front company, Hainan Xiandun Technology Development Co., Ltd. (海南仙盾) (Hainan Xiandun), since disbanded, to operate out of Haikou, Hainan Province.” states DoJ. “The two-count indictment alleges that Ding Xiaoyang (丁晓阳), Cheng Qingmin (程庆民) and Zhu Yunmin (朱允敏), were HSSD officers responsible for coordinating, facilitating and managing computer hackers and linguists at Hainan Xiandun and other MSS front companies to conduct hacking for the benefit of China and its state-owned and sponsored instrumentalities.”
APT40 is focused on targeting countries important to the country’s Belt and Road Initiative (i.e. Cambodia, Belgium, Germany, Hong Kong, Philippines, Malaysia, Norway, Saudi Arabia, Switzerland, the United States, and the United Kingdom).
The APT40 group has been active since at least 2013 and appears to be focused on supporting naval modernization efforts of the Government of Beijing. Threat actors target engineering, transportation, and defense sectors, experts observed a specific interest in maritime technologies.
The cyberspies also targeted research centres and universities involved in naval research with the intent to access advanced technology to push the growth of the Chinese naval industry. The list of victims of the APT40 group also includes organizations with operations in Southeast Asia or involved in South China Sea disputes.
Three of the defendants are said to be officers in a provincial arm of the MSS and one was an employee of a front company that was used to obfuscate the government’s role in the hacking campaigns.
Three defendants, Ding Xiaoyang, Cheng Qingmin, Zhu Yunmin were Hainan State Security Department (HSSD) intelligence officers tasked with coordinating, facilitating and managing computer hackers and linguists at Hainan Xiandun and other MSS front companies. The hackers hired by the trio were involved in hacking campaigns for the benefit of China and its state-owned and sponsored instrumentalities.
The defendants created a front company, Hainan Xiandun Technology Development Co., Ltd. (海南仙盾) (Hainan Xiandun), operating out of Haikou, Hainan Province.
The fourth defendant, named Wu Shurong, was hired by Hainan Xiandun Technology Development to create malware, and hack into computer systems operated by foreign governments, companies and universities. The Chinese nation also supervised the work done by other hackers hired by Hainan Xiandun.
The defendants are charged with one count of conspiracy to commit computer fraud and one count of conspiracy to commit economic espionage, they can face up to five and 15 years in prison, respectively.
 Pierluigi Paganini
Pierluigi Paganini
International Editor-in-Chief
Cyber Defense Magazine

