- Cyber as a Pressure Valve: Why Economic Conflict Is Fueling a New Era of Cyber Escalation
- “2025년 스테이블코인 투자 2024년 대비 10배 예상”···CB인사이츠, ‘스테이블코인 시장 지도’ 공개
- The best portable power stations for camping in 2025: Expert tested and reviewed
- "제조 업계, 스마트 기술 전환 중··· 95%가 AI 투자 예정" 로크웰 오토메이션
- What to Do If You Book a Hotel or Airbnb and It Turns Out to Be a Scam | McAfee Blog
VEC Attacks Alarmingly Effective at Driving Engagement

Vendor email compromise (VEC) attacks are becoming increasingly effective, with engagement rates “worrisomely high,” according to new research by Abnormal AI.
The study, published during Infosecurity Europe 2025, found that VEC messages eclipsed that of business email compromise (BEC) in the EMEA region.
In EMEA, second-step engagement rates from VEC messages exceeded BEC engagement by 90%, at a rate of 47.3%. In addition, repeat engagement was more than twice that of BEC.
Engagement relates to follow-up actions performed by recipients who read the initial email, including replying and forwarding the message.
The report also found that EMEA organizations had the lowest reporting rate for VEC across all regions, at 0.2%. In contrast, they had the highest reporting rate for BEC, at 4.2%.
They also had the lowest rate of second-step engagement with BEC (24.7%).
Both VEC and BEC involve the misuse of a familiar identity to try and trick employees into paying fake invoices or initiating fraudulent wire transfers.
However, unlike BEC, in VEC attacks the person being impersonated is an external third-party, such as a partner or supplier.
In BEC, attackers typically impersonate a senior member of the management team, such as the CEO.
There was a slightly lower VEC engagement rate in APAC (40.2%) and North America (44.4%) compared to EMEA. The global average was 44%.
However, these two regions were far more likely to engage with BEC attacks.
The researchers said this trend could be a result of cultural factors, such as more hierarchical workplace dynamics, meaning a greater likelihood of employees will comply with authority-driven requests – a hallmark of BEC.
Over the 12-month observation period, attackers attempted to steal $300 million via VEC.
The researchers said the findings demonstrate that employees frequently struggle to differentiate between legitimate messages and attacks, especially when those emails appear to come from a known vendor.
Mike Britton, CIO at Abnormal AI, commented: “While VEC volume remains lower than phishing or ransomware, its success rate – and potential financial impact – is far greater, especially as weaponized AI makes it easier than ever for attackers to impersonate trusted vendors.”
He added: “To prevent costly human error, organizations must move beyond reactive training and adopt proactive defences that block threats before they reach the inbox.”
To conduct the study, the researchers standardized the data by using only attacks that were read, eliminating volume as a variable and allowing conclusions to be drawn based on user behavior rather than incident frequency.
Industry and Organizational Variations
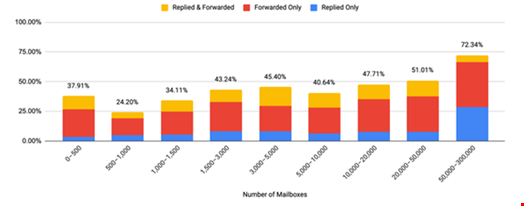
The Abnormal report found that VEC engagement rates increased with organization size.
Among the largest organizations, those with a workforce of 50,000 or more, additional action was taken 72.3% of the time.
In contrast, in organizations with 500-1000 employees, the engagement rate was 24.2%.
One reason large organizations are more vulnerable to VEC attacks may be because of the higher number of third-party vendors they use. This means they are accustomed to receiving email communications from third parties, making it harder to detect impersonations.
The industry with the highest VEC engagement rate was telecommunications, at 71.3%.
The researchers noted that telecoms firms depend on a complex network of vendors, resellers, infrastructure providers and technology partners to deliver services.
Additionally, they typically have large, geographically distributed teams.
This creates an environment in which email is an especially critical channel for coordination between internal teams and external partners.
The industries with the next highest VEC engagement rates were energy and utilities (56.2%), hospitality (55.6%), holding companies (53.6%) and construction/engineering (53.5%).

