WannaRen Returns as Life Ransomware, Targets India

Ransomware
This blog entry looks at the characteristics of a new WannaRen ransomware variant, which we named Life ransomware after its encryption extension.
Read time: ( words)
Although not as well-known as ransomware families such as Ryuk, REvil, or Maze, WannaRen ransomware made a name for itself back in 2020 after it launched attacks against Chinese internet users, infecting tens of thousands of victims. However, it has become relatively quiet since that attack, with the ransomware’s authors even sharing its private encryption key to a security company in August 2020.
In October 2022, we discovered what we initially thought to be a new ransomware, only to analyze it and discover that this may be a resurgence of the dormant WannaRen. This blog entry looks at the characteristics of this new variant, which we named Life ransomware after its encryption extension. Unlike the 2020 WannaRen ransomware attacks that previously targeted China and Taiwan, the attacks from the new variant targeted organizations in India.
The 2020 variant of the WannaRen ransomware was distributed as a malicious PowerShell code bundled with activation tools. The script then obtained a PowerShell downloader which connected to a link to retrieve the malicious ransomware modules. Unlike its previous version, this new variant uses a batch file to download and execute WINWORD.exe to perform DLL side-loading and load the ransomware in memory.
We first discovered the infection under the process of a non-malicious executable WINWORD.exe (the executable file of Microsoft Word). However, further investigation revealed that this infection was a multi-component malware that abuses WINWORD.exe for malicious DLL sideloading (Towards the end of October, we found variants abusing NTSD.exe instead). Furthermore, the actual ransomware is also dropped into the system as an encrypted file, with the attackers using command-line arguments supplied to WINWORD to fetch the ransomware.
Note, however, that incorporating this set of routines in a ransomware attack is not new; we have seen similar approaches in execution by more prominent groups such as LockBit.
WannaRen is also known to have mimicked certain aspects of WannaCry (which it was coined after), particularly in its delivery method: it has been observed in the past using trojanized installers and abusing exploits such as EternalBlue for delivery. (as homage to , which is also where its name was coined after). And after a long hiatus it is back with some new tricks added in its arsenal. Towards the end of October, we even found variants abusing NTSD.exe instead.
In addition to its downloader, the previous version of WannaRen was injected into various processes, including svchost.exe, cmd.exe, mmc.exe, ctfmon.exe, and rekeywiz.exe. This variant, on the other hand, was only loaded in memory to execute its ransomware routine.
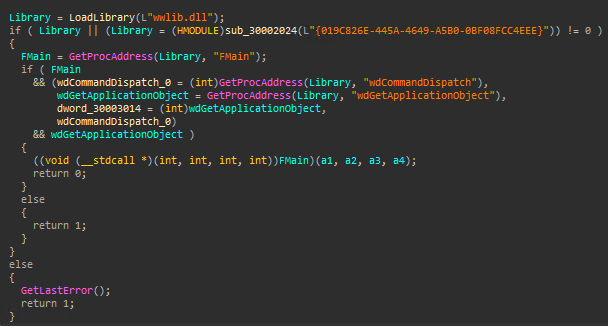
Upon execution, WINWORD.exe will load wwlib.dll and execute its export FMain.
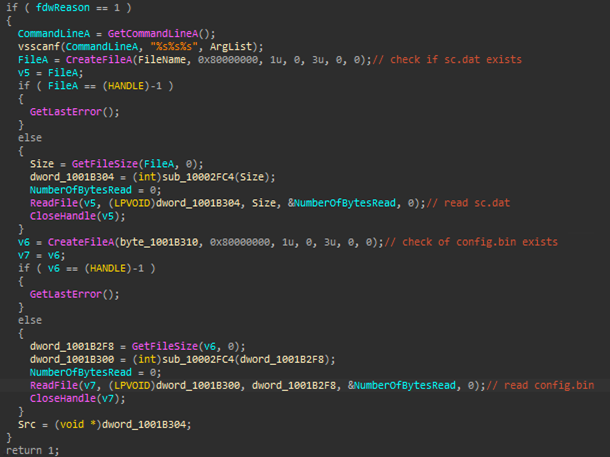
Once loaded, wwlib.dll starts by parsing the passed execution arguments. It first searches for the encrypted shellcode, sc.dat, and checks if the file exists in the same directory where the malicious modules are located. Similar to the shellcode, it also searches for the encrypted ransomware binary, config.bin, and checks if the file exists on the same directory where the malicious modules are located. If found, it uses the decrypted shellcode to load the ransomware in memory and then proceed with its ransomware routine.
Although we have yet to fully verify the correlation between the new WannaRen variant and the use of the Shadow Brokers’ toolkit (aka the leaked Equation Group tools) in this recent attack, it is certainly worth noting that many of the systems affected by WannaRen have the mentioned hacking tools in their system.
It also seems that the entire ransomware package (non-malicious binaries and trojanized DLLs) is being delivered as MSI bundles.
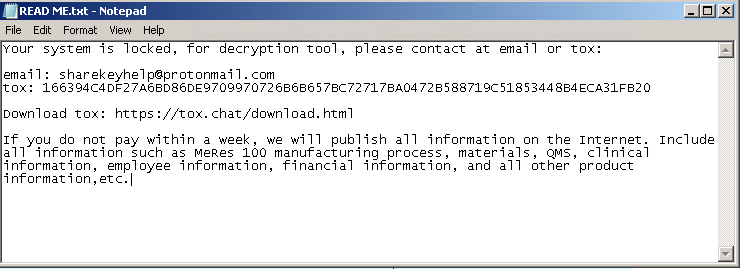
After the Life ransomware encrypts a file, it adds the extension “.life” to it. A ransom note, “READ ME.txt”, is then created in the %Desktop% folder.
Although the initial WannaRen variant was only active for a short time, it managed to cause plenty of damage during that span. With its reemergence as a new variant, it’s possible that the original operators (or malicious actors who have managed to gain access to its code) are looking to expand to other regions.
To defend against ransomware attacks, organizations should consider implementing a multilayered approach to security to protect possible entry points into the system (endpoint, email, web, and network). The following security solutions can detect malicious components and suspicious behavior:
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
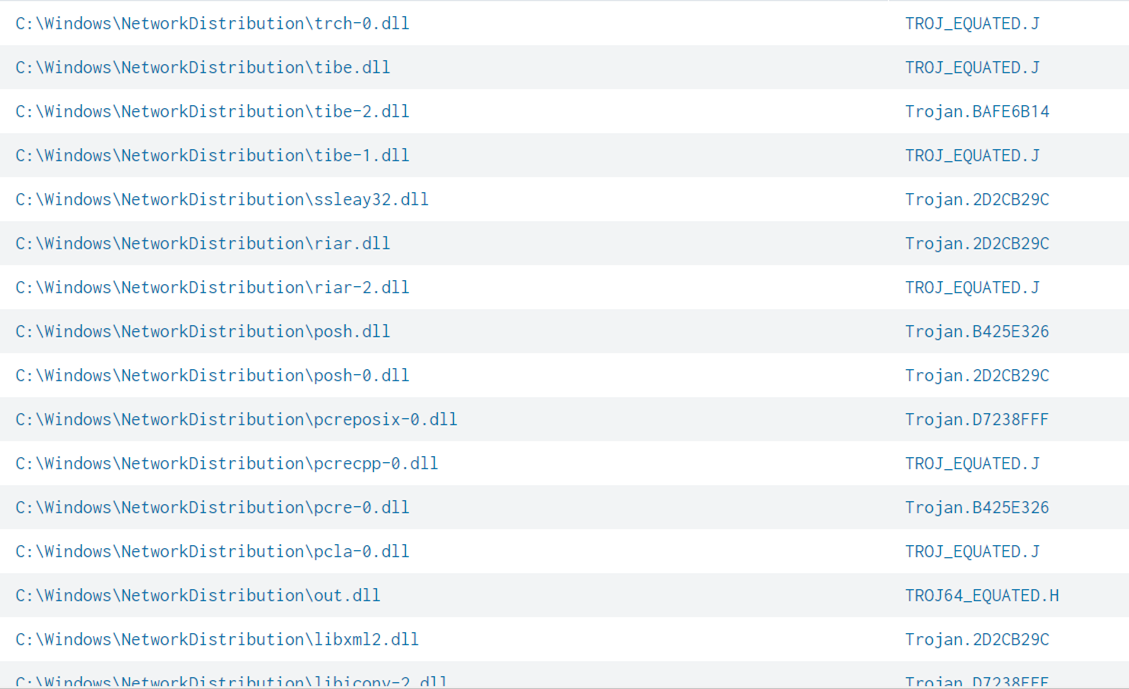
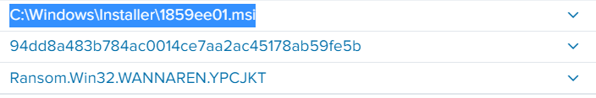
Indicators of Compromise (IOCs)
The indicators of compromise for this blog entry can be found here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk