- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Warning: 1 in 3 employees are likely to fall for a phishing scam

Cybersecurity training company KnowBe4 reports that the number of employees likely to fall for phishing emails drops dramatically with proper instruction on how to recognize an attack.
Image: Vladimir Obradovic, Getty Images/iStockphoto
A new study from cybersecurity training and phishing simulation company KnowBe4 found that one in three untrained users were likely to fall for phishing or social engineering scams.
The report analyzed businesses in a variety of industries to build what KnowBe4 calls an organization’s “phish-prone percentage (PPP),” which indicates how many employees are vulnerable to such attacks. The average baseline, 31.4%, varied greatly by organization size and industry, with a full half of employees in large (1,000+) energy and utilities companies likely to fall for a phishing or social engineering attack (Figure A).
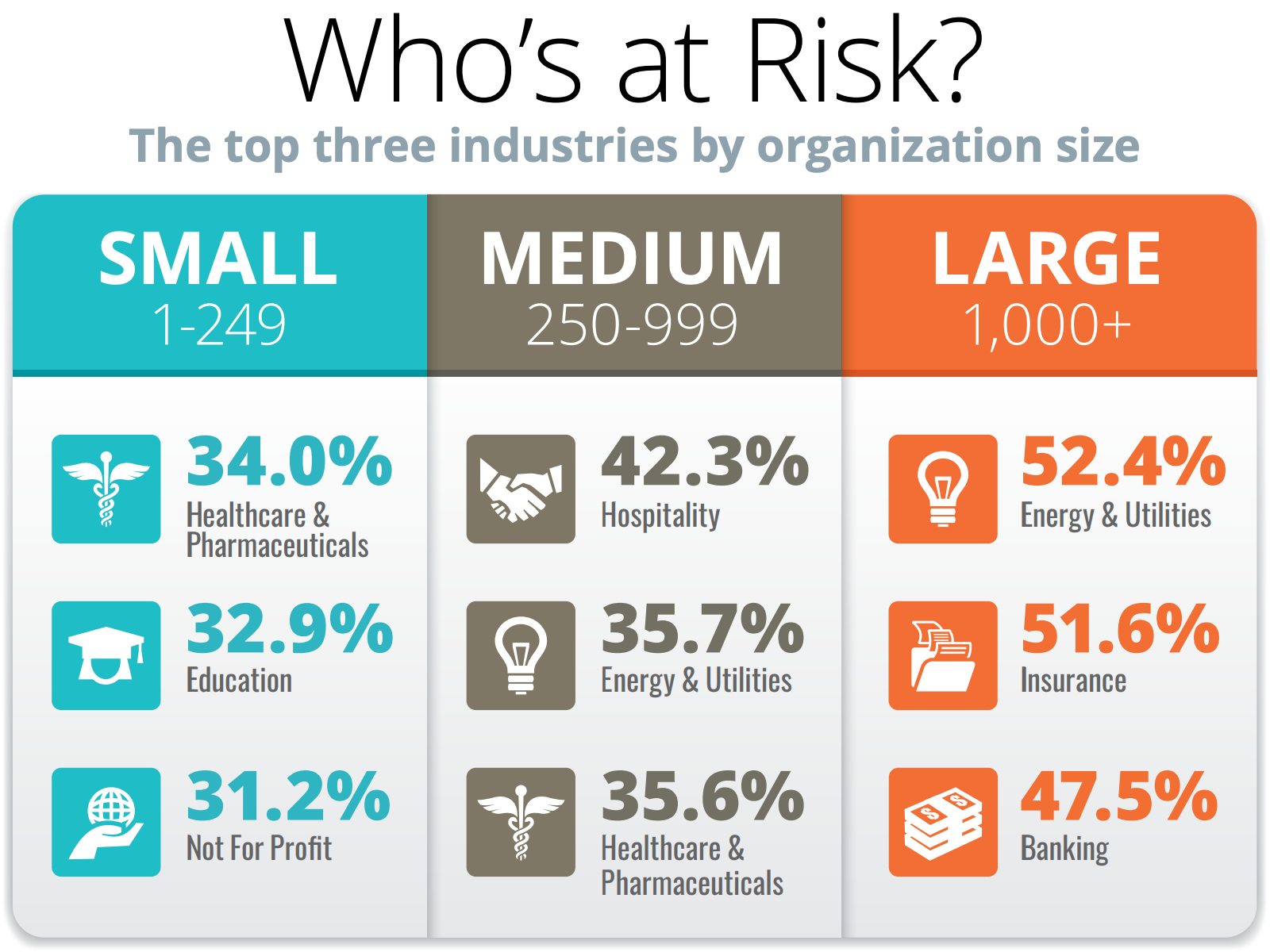
Figure A: The most at-risk industries by organization size, as identified by KnowBe4.
Image: KnowBe4
“This is deeply concerning. Organizations should monitor their risks due to the majority of data breaches originating from social engineering. This data shows us that implementing security awareness training with simulated phishing testing will help to better protect organizations against cyber attacks,” said KnowBe4 CEO Stu Sjouwerman.
SEE: Security incident response policy (TechRepublic Premium)
KnowBe4’s data suggests that training is the answer to the dangerously high percentages. Within 90 days of training, KnowBe4 ran another phishing and social engineering test on the 23,400 organizations included in the report, and it found the average PPP score dropped to 16.4%. After one year of ongoing training that number drops to just 4.8% (Figure B). That equates to an average improvement of 84%, the report said.
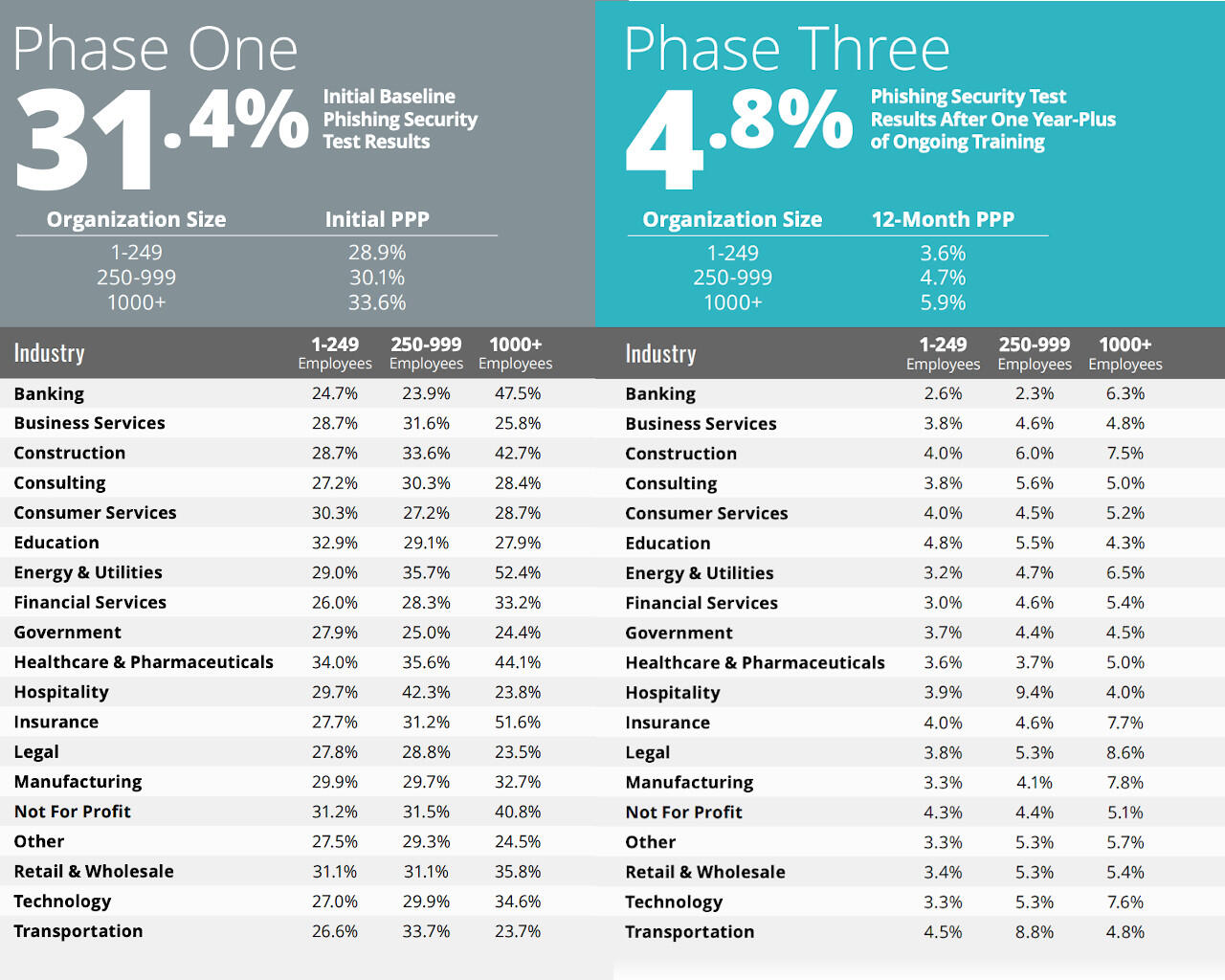
Figure B: Statistics gathered by KnowBe4 that show one year of ongoing phishing/social engineering training and its affect on various industries and organization sizes.
Image: KnowBe4
While the data suggests that training of the type offered by KnowBe4 is effective, training alone can’t be expected to transform an organization. That said, KnowBe4 makes several recommendations for combating phishing and social engineering.
For a start, executives have to model the behavior they want to see in their organizations, KnowBe4 said. The C-suite is a tempting target and a common cause of security breaches due to phishing and social engineering. “Executives should be active participants in all aspects of driving security awareness throughout their organizations, which includes participating in the same security awareness training requirements that the rest of their employees are expected to complete,” the report recommends.
It’s also important for those planning an anti-phishing strategy to partner with the right people, the report recommends. A one-size-fits-all approach to training can be limiting when a lack of deep expertise stops training from being effective. “It may be tempting to leverage your internal training organization to lead this program development … but that will lead to a long-term inability to shape your audience’s security-related thoughts and actions,” the report said.
SEE: How to manage passwords: Best practices and security tips (free PDF) (TechRepublic)
KnowBe4 also recommends that organizations focusing on improving cybersecurity should think like marketers and put cybersecurity front and center in the office, in emails, and non-security training. Constantly reminding employees of the importance of security makes it an unforgettable part of the job.
It’s also essential to define objectives, collect meaningful data and turn that data into usable metrics, simulate phishing attacks, and increase the frequency of training and internal tests to avoid training atrophy, KnowBe4 said.


