- What to Do If You Book a Hotel or Airbnb and It Turns Out to Be a Scam | McAfee Blog
- Cómo evitar la fuga de cerebros en TI
- Is ChatGPT Plus still worth $20 when the free version packs so many premium features?
- How this 'FinOps for AI' certification can help you tackle surging AI costs
- ChatGPT can record, transcribe, and analyze your meetings now
What’s the state of Zero Trust security? – CIO
Zero Trust adoption is accelerating, with over half of organizations reporting they have adopted Zero Trust Security, according to research independently conducted by leading security research firm Ponemon Institute, sponsored by Hewlett Packard Enterprise.
In the report, The 2023 Global Study on Closing the IT Security Gap: Addressing Cybersecurity Gaps from Edge to Cloud, 51% of organizations indicate they have adopted Zero Trust Security strategies. This is a significant increase from similar research released in 2021 when only 20% of organizations indicated they had adopted Zero Trust Security.
Aruba
51% of respondents in a recent Ponemon Institute security study indicated their organizations had adopted Zero Trust Security.
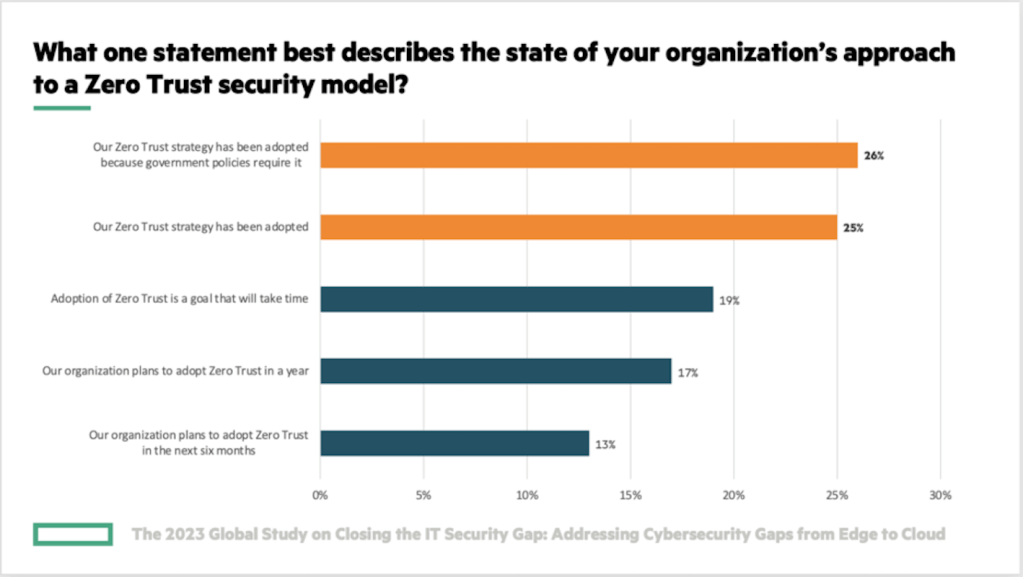
What’s driving the adoption of Zero Trust Security?
Broadening regulatory policies regarding cybersecurity is one driver of Zero Trust Security adoption. 26% of reporting organizations adopted Zero Trust Security because of government requirements, according to the Ponemon study. In addition, many organizations are adopting new models of security to comply with regulations that require limited, controlled access to data, such as the General Data Protection Regulation, Health Insurance Portability, and Accountability Act, and Payment Card Industry Data Security Standard.
Rising cyberattacks are also an ongoing concern. Only 47% of respondents within the Ponemon study rated their organization as very or highly effective in reducing threats in the attack landscape. Organizations are looking for ways to reduce cyberattack risk.
“To minimize risk in a hybrid cloud environment, 44 percent of respondents say it is the implementation of a cybersecurity framework and the modernization of IT security processes that should be a priority,” stated the Ponemon study. “A SASE-enabled IT architecture (42 percent of respondents) and a zero-trust enabled architecture also should be at the top of the list.”
What is Zero Trust Security?
Zero Trust Security strategies limit a user or device’s access to just the resources needed to do their job or fulfill their function, and only if they are not suspected of compromise. Because of this limited and dynamically assessed role-based access security—referred to as least-privilege access—Zero Trust Security can help prevent the lateral spread of attacks and minimize their damage.
Zero Trust Security is not a particular product or solution, but rather an IT security framework. “Organizations with a desire to adopt Zero Trust Security can benefit by taking a look at that next level of detail within their plans,” said Jon Green, Chief Security Officer for HPE Aruba Networking at Hewlett Packard Enterprise. “What have you done to reach that goal? Where else within your environment can you infuse Zero Trust principles?”
How are highly effective organizations addressing Zero Trust Security?
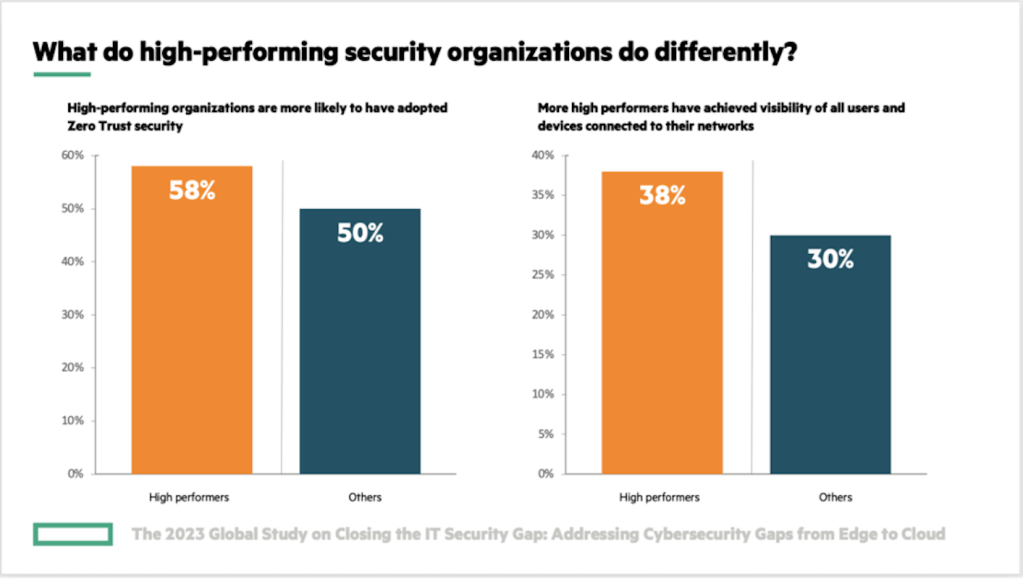
The Ponemon study offered notable insights pertaining to respondents stating their organizations were highly effective in keeping up with a constantly changing threat landscape. These high-performing organizations had fewer security breaches in the past 12 months that resulted in data loss or downtime. The Ponemon Institute analyzed what these organizations are doing to achieve a more effective cybersecurity posture compared to the other 80% of respondents represented in their study.
The Ponemon study revealed that high-performing organizations were more likely to have adopted Zero Trust Security, with 58% of high-performing organizations having adopted Zero Trust Security vs. 50% of other organizations.
In addition, highly effective organizations tended to have greater confidence in their network visibility. High performers are slightly more confident than other respondents that their organizations know all the users and devices connected to their networks all the time.
Aruba
Organizations that report fewer security breaches are more likely to have adopted Zero Trust Security and achieved the ability to know who and what is connected to their networks.
How can you assess your level of Zero Trust Security adoption?
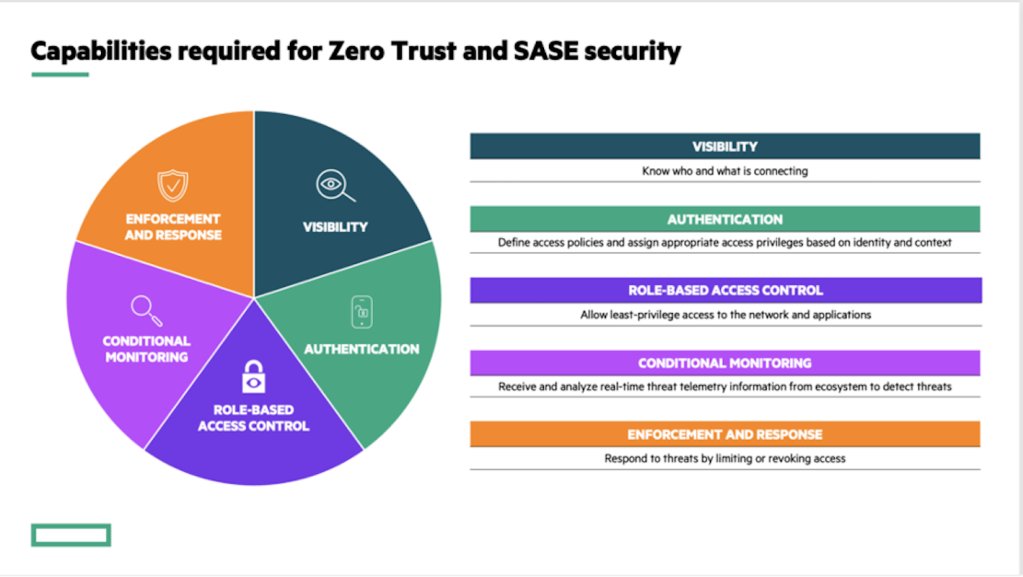
Jon Green advised organizations seeking to adopt Zero Trust Security to evaluate how well they can address the basic capabilities of Zero Trust. “Ideally, you should be able to answer a few questions of every user or device on your network: Who are you? What should you be allowed to do on this network? And how can I enforce that through policy control?”
For a deeper level of detail, consider using this Zero Trust Security checklist adapted from the guide, Implementing Identity-based Zero Trust and SASE Architectures:
- Do you have visibility into every device on your network, even if you do not manage it?
- Do you have consistent methods for assigning privileges to users and devices?
- Are you enforcing standards of security compliance before a device is allowed on the network?
- Are you enforcing role-based access security policies consistently everywhere throughout the network?
- Are you able to continuously monitor a subject’s security state using all available data?
Aruba
Organizations that report fewer security breaches are more likely to have adopted Zero Trust Security and achieved the ability to know who and what is connected to their networks.
Hear from experts on Zero Trust Security
Jon Green and Larry Ponemon, Ph.D., Chairman and Founder of the Ponemon Institute, discussed the findings from the Ponemon Institute report in the webinar, Addressing Cybersecurity Gaps from Edge to Cloud. Watch the webinar on-demand to learn more about the findings in the study and discover how Aruba solutions can address IT security gaps within your organization.
Explore Zero Trust Security in depth
This blog was published on blogs.arubanetworks.com on April 20, 2023.
Use these resources to jumpstart your journey to adoption of Zero Trust Security:

