- The Growing Threat of AI-powered Cyberattacks in 2025
- I test tablets for a living and this is the Samsung tablet I recommend the most
- The Cost of Ignoring Patches: How State and Local Governments Can Mitigate Damaging Security Breaches
- I turned this 98-inch TV into an immersive at-home theater system (and it's $1,500 off)
- You can save $30 on the Apple Pencil Pro right now
Why traditional malware detection can’t stop the latest security threats

Isolating your hardware and your applications is a more effective way to prevent malware from infecting your critical endpoints, says HP.
Getty Images/iStockphoto
Defending your organization against malware used to a matter of running the right antivirus software to detect and block any security threats. But those days are long gone. Fighting today’s more sophisticated and pernicious cyberthreats requires a more advanced approach. In its new Quarterly Threat Insights Report, HP describes the latest types of threats hitting organizations and offers advice on how to more effectively quash them.
SEE: Security Awareness and Training policy (TechRepublic Premium)
The HP-Bromium Threat Insights Report looks at malware observed during the fourth quarter of 2020. To investigate these threats, HP examined the results of customers that used its own Sure Click Enterprise product, which blocks and captures malware and allows it to run in isolated secure containers.
Latest threats
Almost one-third of the malware seen by HP during the quarter was previously unknown, in large part due to the use of packers and obfuscation techniques by attackers trying to evade detection. Some 88% of the malware observed was delivered to the email inboxes of users after bypassing gateway filters. On average, antivirus products took more than eight days to analyze new threats and add them to their definition files.
Among all the malware samples analyzed, Trojans accounted for 55%, largely driven by spam campaigns designed to deploy the Dridex malware. The most common type of malicious file attachments were documents (seen in 31% of the samples), archive files (seen in 28%), spreadsheets (seen in 19%) and executable files (seen in 17%).
“The largest rise was in Dridex campaigns, which is typically used by attackers to deploy ransomware,” Alex Holland, HP senior malware analyst, said in a press release. “Ultimately, any attacker gaining a foothold on an endpoint is bad news—they can use this access to scrape credentials, move laterally between systems, exfiltrate data or sell their access to other cybercriminals—so it creates huge risk for businesses.”
One particularly nasty vulnerability caught by HP during the fourth quarter was CVE-2017-11882, a memory corruption flaw in Microsoft Office’s Equation Editor that accounted for almost 75% of the exploits caught by HP. Another one was CVE-2017-0199, which runs malicious scripts that deploy malware when a user opens an Office document.
A trend spotted by HP involved a new Office malware builder called APOMacroSploit designed to deploy Remote Access Trojans (RATs). In this one, the attackers send out spam emails that try to trick the recipient into opening an Excel attachment. Opening the file installs BitRAT on the computer, which the attackers can use to view webcam activity, log keystrokes, mine cryptocurrencies, and download more malicious files.
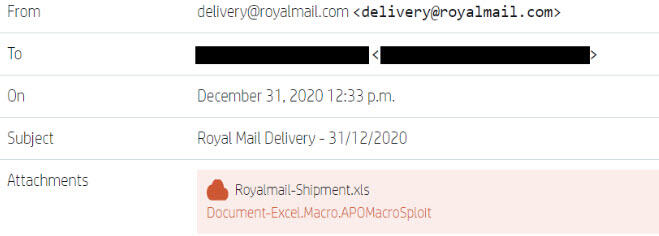
Malicious spam email containing APOMacroSploit malware
Image: HP
“Low-cost malware-as-a-service kits are an attractive prospect to cybercriminals, and we have seen these continue to proliferate in underground forums,” Holland said. “Kits like APOMacroSploit, which emerged in Q4 2020, can be bought for as little as $50, illustrating just how low the barrier to entry is for opportunistic cybercrime.”
During the fourth quarter, Emotet also breathed one last gasp before its takedown in January 2021. The criminals behind this infamous botnet altered its downloader using DOSfuscation techniques to avoid detection. The downloader also flashed an error message when opened, atypical behavior for a malicious document.
How companies can protect themselves
Attackers keep finding new ways to bypass detection controls, so trying to detect every threat is futile as something will always slip through, Ian Pratt, Global Head of Security for Personal Systems at HP, said in the press release. As a result, more organizations are looking to integrate zero-trust principles into their security defenses.
“Relying on detection alone will only result in an unsatisfactory outcome for the organization, so a more architecturally robust approach to security is required; one that builds protection in from the hardware up,” Pratt said.
“Hardware-enforced technologies like micro-virtualization are transparent to the end user—this means they can click on email attachments and download files as they normally would, but are safe in the knowledge that if anything is malicious, it is rendered harmless,” Pratt said. “This protection-first approach leaves hackers with nothing to steal and no way to persist, helping organizations to deal with the variety of threats cybercriminals will throw at them.”
Specifically, Pratt advises organizations to use application and hardware isolation to prevent malware from doing damage.
“Application isolation through virtualization applies least-privilege access to risky activities on the endpoint, rendering malware harmless by isolating it in micro-virtual machines,” Pratt said.
“Hardware-enforced isolation removes the opportunity for malware to cause harm to the host PC–even from novel malware–because it does not rely on a detect-to-protect security model,” he added. “By having security built in at the hardware level, endpoint devices can help to defend users and recover from attacks automatically, improving business resiliency.”


