- This 5-in-1 travel charger is the only one I'll need this summer (and it's full of power)
- You can turn your Google Search into a podcast now - here's how
- Why I'm switching to VS Code. Hint: It's all about AI tool integration
- The Impact of Quantum Decryption
- The augmented IT team: How AI is reshaping IT roles and skills for the future
With Cloud the Norm, Insiders Are Everywhere — and Pose Greater Risk
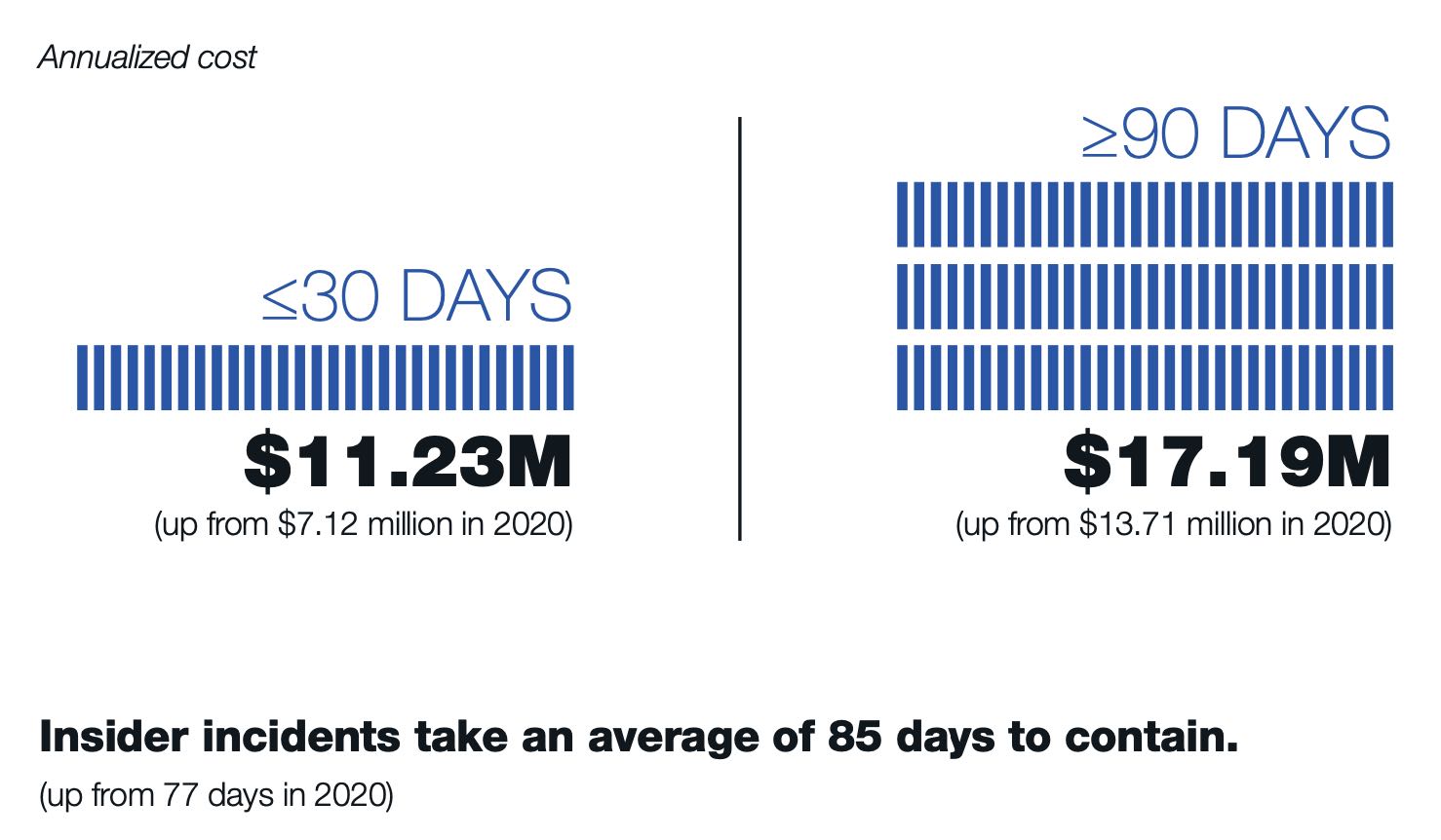
Organizations dealing with insider threats spent $15.4 million on average during 2021, a 34% increase from 2020, and required 85 days to contain each incident, according to a survey of 1,000 information technology and security professionals released on Jan. 25.
The survey, conducted by the Ponemon Institute and sponsored by enterprise security firm Proofpoint, documented 6,803 total insider incidents, including those caused by negligent employees, malicious insiders, and the theft of credentials by outside hackers. Because companies have accelerated their move to cloud services in the wake of the pandemic, the theft of credentials has become a more common — and the most expensive — insider threat, nearly doubling in frequency over the previous year.
The move to remote work and cloud services has changed the way that companies have to watch out for insider attacks, says Ryan Kalember, executive vice president of cybersecurity strategy for Proofpoint.
“The relationship with the employer is different, and the set of technical controls you use to identify those incidents are different,” he says. “There are no classic insider risk program elements when you are not all going to the same office, and can say, ‘Oh, that guy is acting funny.’ You can’t do that when everyone is meeting over Zoom all day.”
Based on a sample of 278 companies, the survey found that the insider attacks cost companies in North America the most, with the average firm in that region paying $17.5 million per year; the financial services industry had the greatest cost, with each company paying $21.3 million on average, according to the report.
Overall, 43% of the cost from insider threats was due to negligent employees, 27% due to malicious insiders, and 30% due to credential theft. The most common insider incident, negligent insiders, accounted for 56% of the incidents but cost the least — about $485,000 — to remediate on average, while the least common type of insider incident, credential theft, which accounted for 18% of incidents, cost the most, at $805,000.
Both the frequency and cost per incident of insider threats have increased over time, Larry Ponemon, chairman and founder of the Ponemon Institute, said in a statement.
“We are seeing the risk of malicious insider threats increase — with more users accessing business data from outside the confines of the office,” he said. “This can blur the security team’s ability to identify and differentiate between well-meaning employees and malicious insiders trying to siphon sensitive business data.”
User-Credential Theft
Perhaps unsurprisingly, the theft of an employees credentials remains the most significant threat.
More than half of security professionals (55%) interviewed during the survey consider the theft of an employee’s valid credentials as the most significant concern, while about a quarter (24%) worry about criminal or malicious insiders and a fifth (21%) worry about careless or negligent employees.
“Someone loses control of their credentials, especially things like VPN credentials, that is just a nightmare to track down,” says Proofpoint’s Kalember. “It’s not a traditional insider threat, but the compromised insider caused one of the more painful incidents because of how VPNs work in a work-from-anywhere world. It is hard to take those legitimate set of creds and figure out everything that was done with it to make sure that data was not lost.”
Malicious insiders, the second most common threat and second most expensive to remediate, generally used email to steal sensitive information. About two-thirds of professionals indicated that email contained the most sensitive data, including personally identifiable information (PII) and intellectual property. Email is also used to exfiltrate data, with about three-quarters (74%) of respondents believing that malicious insiders used email to send sensitive data to third parties.
The average incident took 85 days to resolve, with a little more than half of companies taking from between one month and three months to resolve an insider attack, according to the survey. Only 12% of companies mitigate an insider incident in less than a month.
Most companies have focused on using data loss prevention (DLP) tools, privileged access management (PAM) software, and user and entity behavior analytics (UEBA) systems to mitigate the risk, according to the survey. About two-thirds (64%) of respondents use DLP systems to prevent access to and exfiltration of sensitive data, while 60% closely manage highly privileged accounts using PAM software.
Business disruption accounted for nearly a quarter of the cost (23%) of incidents, while technology accounted for 21%.

