- This Eufy robot vacuum has a built-in handheld vac - and just hit its lowest price
- I highly recommend this Lenovo laptop, and it's nearly 50% off
- Disney+ and Hulu now offer prizes, freebies, and other perks to keep you subscribed
- This new YouTube Shorts feature lets you circle to search videos more easily
- I replaced my Kindle with this E Ink tablet that runs Android - and don't regret it
You have A Choice How to Deploy Silver Peak Integrated Orchestration with Palo Alto Prisma Access Cloud Security

Many Silver Peak SD-WAN customers have adopted Palo Alto Prisma Access cloud-delivered security services. You might be wondering how you can make Silver Peak and Palo Alto work together to take advantage of secure local Internet breakout from your branch or remotes sites to maintain both the performance and security of your business applications.
The Silver Peak Unity EdgeConnect™ SD-WAN edge platform integration with Palo Alto Networks’ Prisma Access cloud-delivered security enables enterprises to shift to a secure access service edge (SASE) solution. The joint solution can be deployed via two different integration methods, both centrally managed within the Silver Peak Unity Orchestrator™ management console. I will use the analogy of the red or blue pill from the movie The Matrix: “Do you want the red pill or the blue pill?” The choice is yours, either will work, but each is meant to enable a different type of deployment. In this blog, I will discuss both integration methods, how they work and when to choose each option. I’ll also provide a link to a technical video that demonstrates both deployment methods.
Silver Peak recently published a detailed guide that describes how to service chain EdgeConnect to a Palo Alto firewall, and Palo Alto Networks has also published a similar Silver Peak SD-WAN Solution Guide that documents how to configure pass-through tunnels from the Orchestrator console. Both guides describe the red pill – the first method. The blue pill – or second method – is to use a YAML file with the Orchestrator pre-configuration wizard. The second method is not yet covered in the configuration guide, so I will describe it here and provide a link to a video demonstration.
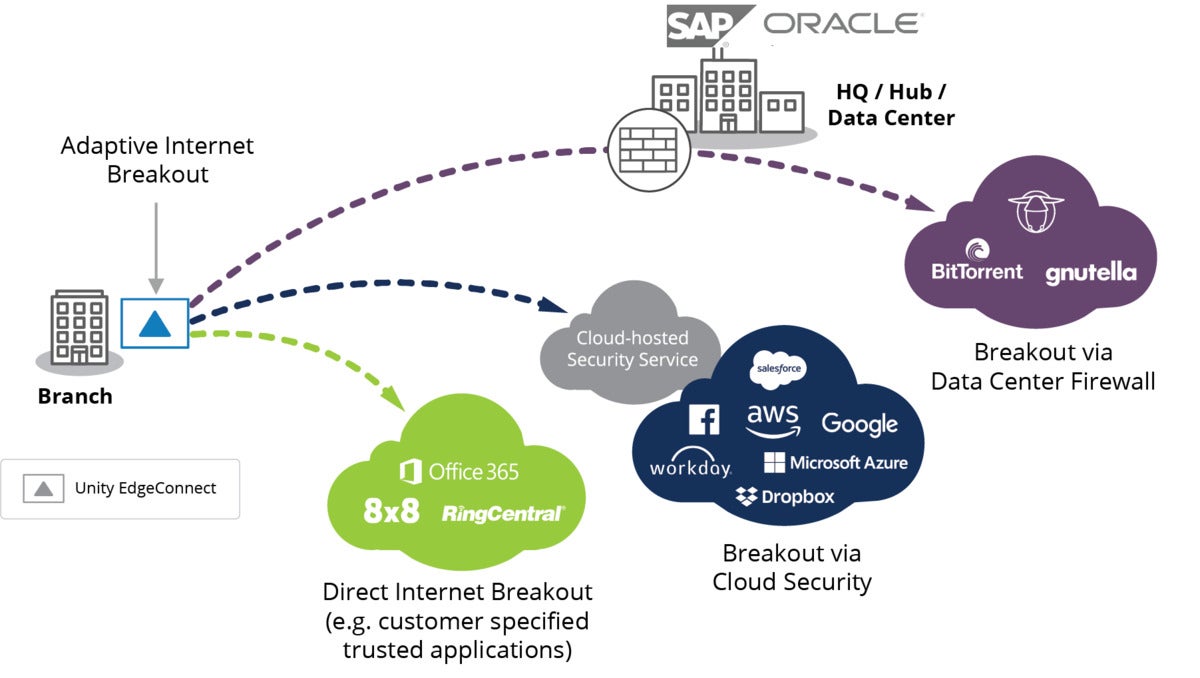
When adopting SaaS applications such as Office365, Salesforce, Box, Atlassian and others, it’s important that users connect directly to the nearest point of presence for the SaaS provider. This delivers the highest quality of experience to application users. It’s also important to ensure the application traffic directed to the internet from the branch location(s) is secure. To achieve this, you’ll need to answer two questions.
Both questions are important, and if we do not configure policies correctly, users will experience sub-optimal application performance and quality of experience. Why? because if traffic traverses a longer route to reach the SaaS point of presence application response will be sluggish and less responsive to the end user. With traditional router-centric networks, application performance suffers when traffic is backhauled to the data center firewall for security inspection prior to being directed to the public cloud, commonly referred to as the trombone effect. This added delay negatively impacts performance and the quality of experience for the end user. And an incorrect security policy can expose the enterprise to security breach.
The integration of the Silver Peak EdgeConnect platform with the Palo Alto Prisma Access cloud-delivered security service enables secure local internet breakout from branch or remote locations and eliminates the need to backhaul cloud-destined traffic to the data center. An instance of Palo Alto Prisma Access located as close to the user as possible inspects and secures application traffic before forwarding it on to the SaaS provider.
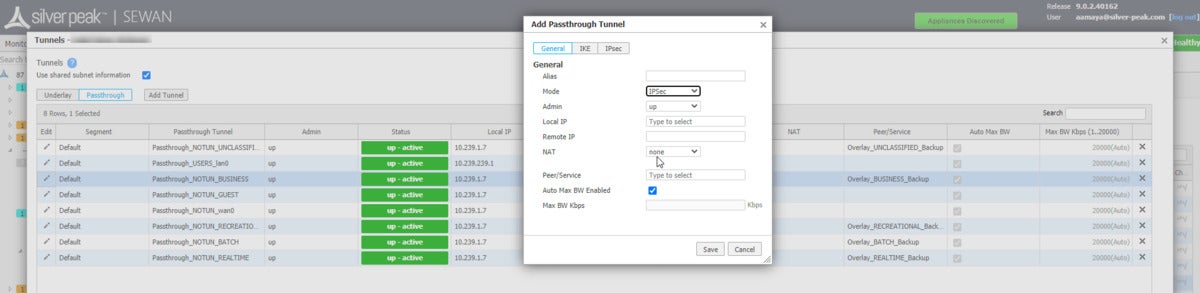
With Silver Peak, enterprises can automatically steer traffic in accordance with security policy and business intent. A sample security policy might look something like this: To get started, we first must configure Prisma Access. Using Palo Alto Panorama, we will configure the remote networks which can be accomplished following these instructions: Configure Prisma Access for Networks. The workflow will push the policy configuration to the cloud service and automatically onboard each remote site onto the network. Once the policy is applied traffic will be sent from the remote sites through the primary and secondary IPsec tunnels created to Prisma Access. Next, we configure the remote network between the Silver Peak SD-WAN and Prisma Access by configuring the remote network tunnels. From Orchestrator, we configure the passthrough tunnels from the “Tunnels” configuration menu to the Palo Alto Prisma cloud security service.
 Silver Peak
Silver PeakGoing back to The Matrix analogy, the red pill is a single site configuration, and deployment is straightforward using standard network administration practices. This method enables network administrators to be selective with the configuration. It can also be employed to create unique configurations for specific locations as desired. This is useful for small numbers of locations that must be brought online, but do not require physical firewall hardware and are to be secured by a cloud-delivered security service.
 Silver Peak
Silver PeakFigure 3. Tunnel Passthrough configuration settings
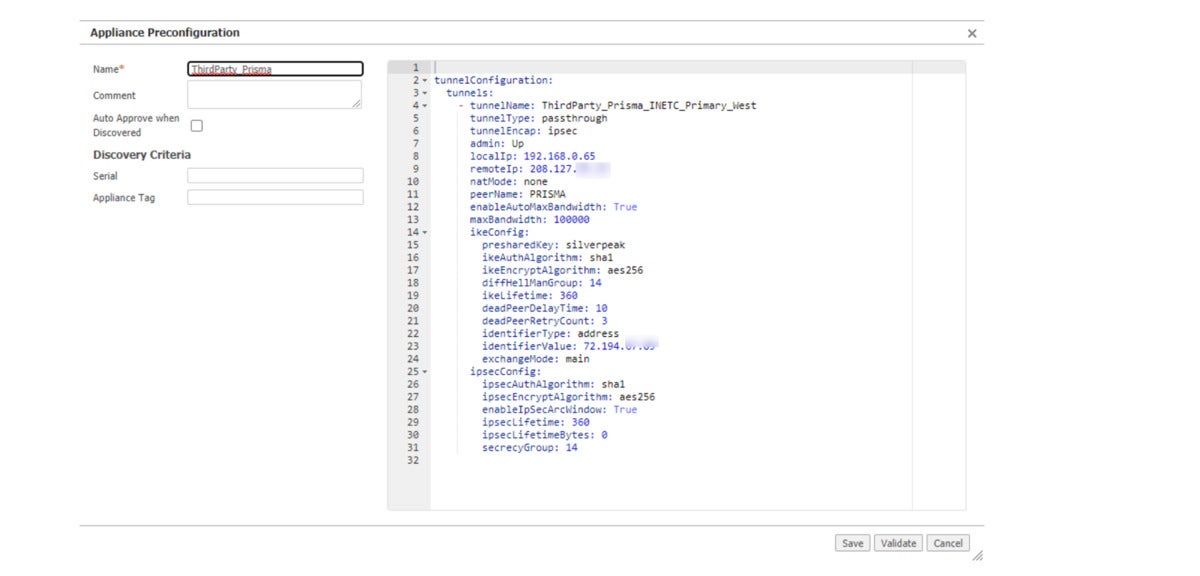
The second method – the blue pill – is for large deployments from 100s to 1000s of sites. The method employs a pre-configuration file using the Silver Peak deployment Configuration Wizard. In a matter of minutes, a pair of secure IPsec tunnels to Prisma Access enforcement points are created using a pre-configured YAML file. The blue pill delivers an automated configuration, enabling the seamless configuration of Prisma Access cloud-delivered security services. By using the pre-configuration files, dozens or thousands of sites can be quickly and consistently configured. The method is commonly used for large scale deployments where many of sites will all be configured identically. Instead of configuring one site at a time as described in the previous “red pill” method, IT can quickly generate a pre-configuration file and deploy it with a few mouse clicks to hundreds or thousands of sites. If there is requirement for several different security policy profiles, it is also possible to create several pre-configuration files with different settings for each and deploy them selectively to branch locations.
 Silver Peak
Silver PeakFigure 4. Sample Pre-Configuration file to connect to our Primary West Prisma cloud security
So, which pill is best for your solution? You can’t go wrong with either one. By selecting the right SD-WAN platform, you can achieve the full transformational promise of the cloud, cloud-delivered security and SD-WAN.
The Silver Peak integration with Palo Alto Prisma Access simplifies the deployment process for a modern cloud-delivered security service, significantly reducing the time and resources required to configure the tunnels. To learn more, watch the video how EdgeConnect SD-WAN integrates with the Palo Alto Prisma Access cloud security service using either configuration method.
For the third consecutive year, Silver Peak has been recognized as a Leader in the 2020 Gartner Magic Quadrant for WAN Edge Infrastructure. Get the full report.
Copyright © 2020 IDG Communications, Inc.

