- One of the best cheap Android phones I've tested isn't made by Samsung or TCL
- One of the best portable speakers I've tested projects booming sound (and it's 40% off)
- Grab a Microsoft Office 2019 license for Mac or Windows for $28
- Buy or gift a Babbel subscription for 74% off right now
- Data Breaches are a Dime a Dozen: It’s Time for a New Cybersecurity Paradigm
Detect Azure AD Hybrid Cloud Vulnerabilities

Workload Security
AADInternals is a PowerShell module widely used by administrators for administering Azure Active Directory (AD) and Microsoft 365 – learn how to protect against their common vulnerabilities.
May 19, 2022
Read time: ( words)
What is AADInternals?
AADInternals is a PowerShell module widely used by administrators for administering Azure Active Directory (AD) and Microsoft 365. As the name suggest it deals with integration of Azure AD for on-prem and cloud services. More features can lead to more security issues, which might be leveraged by threat actors for malicious purposes like creating backdoor users, stealing passwords, stealing encryption keys.
AADInternals and Azure AD
Many companies benefit from moving to the cloud, but still want to keep parts of infrastructure on-premise to keep full control. This also includes Azure AD—some services hosted in the cloud need it for proper functionality and/or it can provide secure remote access to applications used by external users. This integration extends the possible attack surface and adds complexity to the entire deployment. This blog explores possible misuses of legitimate tools—like AADInternals— in hybrid-cloud environments and how to detect them using Trend Micro Cloud One™ – Workload Security.
Common misuses of AADInternals
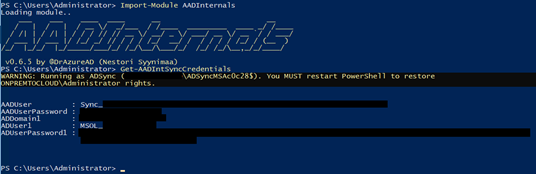
While AADInternals is a completely legitimate and handy tool, it often can be exploited by malicious actors if some specific actions and/or commands are used. For instance, when you synchronize the identity data between the on-premises AD and Azure AD, Azure AD Connect application is used on on-premises AD, enabling an attacker to compromise this service and extract information from the targeted Azure AD tenant.
Once attacker has foothold on Azure AD connect servers, they can perform variety of the operations, including:
- Dumping encryption keys
- Exfilteration of Azure AD connector account password
- Creating backdoor to Azure AD
- Update Azure AD Connect credentials for Azure AD
- Create users only in Azure AD
Detections for AADInernals:
Now that we understand how these legitimate tools and services can be exploited, let’s explore how to detect potential attacks using Workload Security and Trend Micro Vision One™.
Part of our unified cybersecurity platform, Trend Micro Cloud One™ is a security services platform for DevOps teams composed of seven services. It integrates with Trend Micro Vision One, which leverages industry-leading XDR capabilities to collected, correlate, and display data from Trend Micro Cloud One in a straightforward dashboard. Think of Trend Micro Cloud One as the security camera, and Trend Micro Vision One as the app on your phone where you can see the video stream and any alerts.
In this demo, we used Workload Security to detect potential vulnerabilities. Workload Security ensures your containers and datacenters are secured with automated scanning and customizable post-scan actions. Let’s explore detections made by Workload Security:
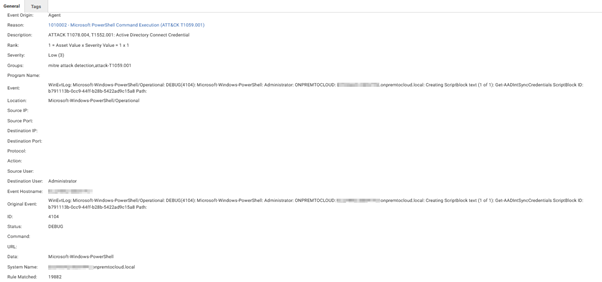
1. Log Inspection
Through this module we can tap into PowerShell activity events on the host. Upon the execution of AADInternals commands an analyst can monitor these commands with 1010002 – Microsoft PowerShell Command Execution (ATT&CK T1059.001).
2. Activity Monitoring
The module can detect process, file, AMSI and network activities on endpoints running Workload Security. In this case, we will examine the AMSI activity since there is no network or file activity in this scenario. Activity monitoring module looks for some of these objects:
a. SQL Client connector object: System.Data.SqlClient.SqlConnection
b. Registry key to fetch ‘AD Sync’ details from: ‘HKLM:SOFTWAREMicrosoftAD Sync’
c. DLL file used by AD Sync tool: ‘mcrypt.dll’
Tying it all together with Trend Micro Vision One
Trend Micro Vision One takes all the detections from Workload Security and correlates them to provide comphrensive visibility across all data in one console. Let’s dive into what you can see (pun intended) with Trend Micro Vision One:
1. Search App
To hunt down potential use of AADInternals in the environment, analysts can use queries such as:
a. eventSubId:”901″ AND processName:powershell AND objectRawDataStr:”AADInternals”
b. eventSubId:”901″ AND processName:powershell AND objectRawDataStr:”ADSyncSyncCycle”
c. eventSubId:”901″ AND processName:powershell AND objectRawDataStr:”Get-AADIntSyncCredentials”
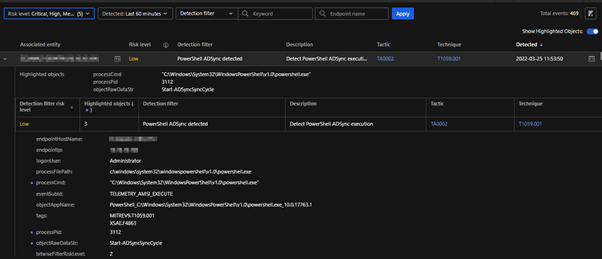
2. Observed Attack Techniques (OAT)
OATs are generated from individual events that provide security value. To investigate the possible use of AADInternals tools, analysts can look for these OAT IDs derived from many other OAT triggers to indicate suspicious activities on the affected host.
a. PowerShell ADSync detected
b. Identified AADInternal Suite Commands To Access Azure AD Credentials
c. Identified Credential Operation Using Azure AD Internals Tool
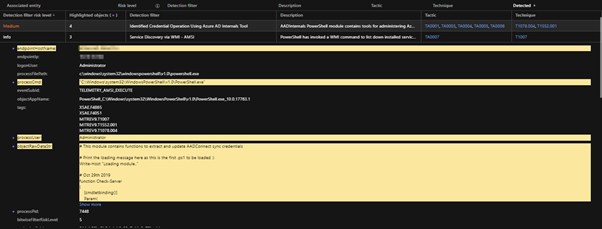
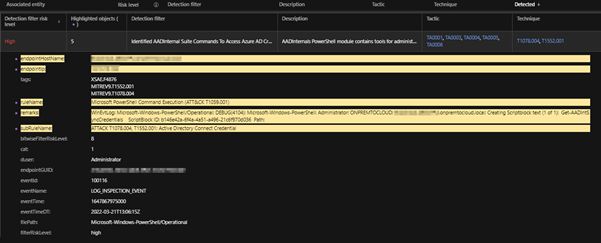
Workbench
The Trend Micro Vision One Workbench app helps analysts see significant correlated events based on occurrences throughout the entire fleet of workloads. The left side of the diagram shows the summarized sequence of events where analysts can view the different fields of interest that are considered important and dive deeper into provide the scope of the attack on the right.
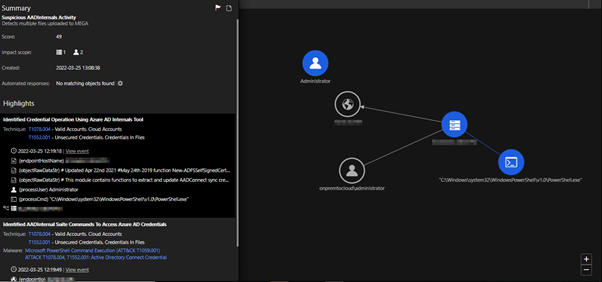
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk


