Silver Optis: Innovative and Socially Conscious Technologies at Black Hat

By Olivia Gallucci, Cybersecurity Reporter, Cyber Defense Magazine
I interviewed approximately sixty industry leaders from over forty companies who attended Black Hat. Although this article series—The Optis—can be read as a traditional Black Hat recap, I specifically highlight twenty-one companies that stand out and whose growth I recommend watching.
Rochester Institute of Technology’s Cybersecurity Club, RITSEC, inspired the metrics I used to analyze and rank companies. Specifically, I adopted RITSEC’s motto, “Security Through Community,” while examining each company’s ability to promote social good, inclusion, and innovation inside and outside of the company. Furthermore, I referenced materials—public demos, open-source code, and publications—to determine the accuracy of the company’s claims and the span of its communal reach, public contributions, and social good.
Given Cyber Defense Magazine’s awarding of unicorns (“a private company with a valuation of over $1 billion”) and that Olympic sailing occurred during Black Hat, I created a conceptual framework—The Optis Series—to highlight innovative and socially conscious companies at Black Hat USA 2021 (UserGuiding). The Optis Series contains three articles: bronze, silver, and gold. You can learn about the judging criteria I used for the Optis Series here or scroll to the end of this article.
CyberGRX
Dave Stapleton, CISO of CyberGRX
CyberGRX is a software as a service company using a varied source of data to manage and analyze third-party security risks. Specifically, CyberGRX uses an exchange model of data to provide organizations with a dynamic stream of third-party data and advanced analytics so clients can efficiently manage, monitor, and mitigate risk in their partner ecosystems. Its goal is to connect every company with the exchange system to increase global understanding of third-party risk inheritance and promote the disclosure of security risks in business agreements.
The exchange model is CyberGRX’s innovative key. Its platform is the largest risk exchange platform globally and contains thousands of risk assessments, allowing organizations to quickly identify which third parties pose the highest cyber risk and help those third parties and organizations alike focus their resources on critical areas. Thus, CyberGRX’s clients gain a better understanding of third-party assessment data, enabling them to derive logical risk insights, make informed business decisions, and save thousands of hours spent on assessment chasing.
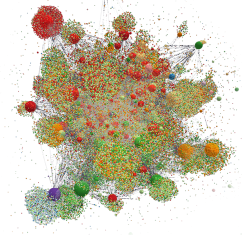
3D depiction of a third-party ecosystem demonstrating the interconnectedness of organizations today. Used with permission from CyberGRX.
CyberGRX provides visibility into clients’ third-party ecosystems, so they can determine which third parties are missing the controls needed to respond to emerging threats like ransomware and extortionware. Its analysis promotes accountability and shared responsibility by allowing third-party risks to become a first-party responsibility. When companies know their third parties are vulnerable, they can help those parties with remediating vulnerabilities in critical areas. CyberGRX’s mission promotes knowledge and growth in cybersecurity, and its platform provides new security insights which have not been available before.
Digital Shadows
Alastair Paterson, CEO and Co-Founder of Digital Shadows
Founded in 2011, Digital Shadows focuses on digital risk and threat intelligence. It specializes in identifying data loss like intellectual property, customer data, and credentials. Digital Shadows created one of the largest credential databases globally, hosting over 25 billion entries. Digital Shadows’ sales increased over fifty percent from last year, and it expects to hire around twenty employees by the end of 2021.
Digital Shadows’ platform alerts clients of data leakages on code-sharing sites like GitHub, GitLab, and Bitbucket. These leakages often stem from things like accidentally publishing code and leaving keys open. It also can detect when file stores are accidentally shared (i.e., Amazon S3 buckets).
Used with permission from Digital Shadows.
Lastly, Digital Shadows can detect brand impersonations. For example, oliviagallucci.com is my website; if an adversary created oliviagalucci.com (one l), Digital Shadows would disclose the event to me. Its platform can also detect fake apps and social media profiles.
Used with permission from Digital Shadows.
Digital Shadows uses multiple open-source tools; Spring Framework, Guava, Terraform, Apache HBase, and Jenkins are a few notable ones. Paterson stated that “Digital Shadows began open-sourcing some of its projects after our security research team discussed how we could give back to the community.” One of Digital Shadows’ notable repositories is Orca, an asset discovery tool. Paterson continued, “One of our goals is to integrate into the open-source community to foster collaboration and constructive feedback,” and Digital Shadows is well on its way to achieving this goal.
ExtraHop
Jeff Costlow, CISO of ExtraHop
ExtraHop is a network detection and response (NDR) provider, helping organizations secure environments and implement threat protections. ExtraHop specializes in detecting lateral movement and increasing the effectiveness of high-speed networks. Its goal is to bridge the gap between SIEM and EDR across client networks to help organizations detect and respond to advanced threats.
ExtraHop DNS LAM. Permission to use from ExtraHop.
ExtraHop’s innovation stems from its Reveal(x) 360, a software as a service platform utilizing cloud-scale artificial intelligence to analyze adversaries in real-time. Reveal(x) 360 works at the network level and analyzes up to 100 Gbps. Furthermore, ExtraHop’s behavioral network analytics detect approximately 1500 high-risk threats per month, including supply chain attacks, APTs, and Zero Days. Reveal(x) 360 is able to decrypt traffic to provide complete visibility and enable deep forensics investigations. Reveal(x) 360 also can see activity without being detected, so bad actors don’t even know that they are being watched. This is an important part of ExtraHop’s NDR solution, given that recent highly sophisticated attacks like SolarWinds SUNBURST have brought awareness to the fact that hackers are learning to evade traditional security methods and tools.
ExtraHop overview. Permission to use from ExtraHop.
ExtraHop regularly contributes cyber threat data and anonymized threat intel identified via their platform to the security community. Key contributions include ExtraHop’s research on the techniques used in the SolarWinds Sunburst attack to evade detection as well as the company’s research on connected devices during Covid-19. ExtraHop also contributed to the latest version of the MITRE ATT&CK Framework and Knowledge Base, which now includes the latest developments in network detection and response methodologies. By sharing the growing body of network attack behaviors in the MITRE ATT&CK framework, security teams are now better equipped to detect and respond to advanced threats as they integrate NDR Into their security operations. The MITRE ATT&CK framework is natively integrated into the ExtraHop Reveal(x) 360 interface, which further helps security professionals detect the latest tactics, techniques and procedures being used by adversaries on their networks. ExtraHop’s security research team regularly shares threat briefs, which are immediately available to customers via the product and also published publicly on ExtraHop’s blog.
Learn more: Why Cyber Defense Needs Software Behavior Transparency by Ben Higgins, Distinguished Software Engineer at ExtraHop
GuidePoint Security
Tony Cook, Head of Threat Intelligence
Mark Lance, Senior Director of Cyber Defense
Victor Wieczorek, VP of Application Security and Threat & Attack Simulation
GuidePoint Security is a peer-play security consulting and management company. It has spread from its east coast beginnings to expand across most of the United States. GuidePoint’s focus is solving complex problems from a consultative approach. Its innovativeness stems from its unique company model. GuidePoint Security provides cybersecurity solutions and services through a localized team within that region, with additional teams providing capabilities across the entire nation.
Unlike many companies, GuidePoint Security does not promote sponsored products because it is not a vendor. GuidePoint Security endorses quality products to ensure productivity and client satisfaction.
GuidePoint Security is heavily involved in the open-source community and prides itself on its communal outreach and diverse solutions. OSS is built into or surrounds most of its tools, and as a result, its teams have become effective contributors, analyzers, and creators of OSS. One of its notable projects is RedCommander, a red team infrastructure complete with Redirectors and basic domain fronting. GuidePoint Security also contributes to open source communities such as Velociraptor, BloodHound, MISP, and others.
GuidePoint employs approximately five hundred security professionals and expects to hire around one hundred people within the following year. For those interested in working with GuidePoint Security, the senior leaders stated that “we want people who are hungry to learn, care about the quality of their work, and are passionate about security in their free time.” In the future, GuidePoint Security is focusing on developing automation and productivity tools to ensure that “smart people are doing smart things.
Follow GuidePoint Security on LinkedIn here.
NTT
Setu Kulkarni, VP of Corporate Strategy & Business Development
Bruce Snell, VP of Security Strategy and Transformation
NTT is a global technology services company. As a global information and communications technology provider, the company employs about fifty thousand people across 57 countries. I interviewed two NTT executives—Setu Kulkarni and Bruce Snell—about their team’s latest developments.
Learn more: NTT’s Virtual Reality SOC Tour
NTT’s Security Division functions as a managed security services provider (MSSP), supplying talented professionals and diverse vendor relationships to its clients so that they can focus on running the business and leave everything from security operations to threat monitoring and intelligence to incident response to their NTT team. Furthermore, around forty percent of internet traffic runs through NTT, which gives their specialists unmatched expertise in malicious traffic and vulnerability analysis. Bruce describes it as “watching the weather patterns of cybersecurity.”
NTT’s Application Security (AppSec) team utilizes an innovative consumption model, factoring in clients’ budget and regulatory needs; it offers an AppSec platform, technical expertise, and training. Its AppSec platform helps clients detect, track, and remediate vulnerabilities on all of their devices. NTT’s AppSec team also tracks open-source software (OSS) vulnerabilities and assists clients with OSS remediation. When OSS vulnerabilities are particularly problematic, NTT proposes remediations to the original OSS project.

Olivia Gallucci (CDM) interviewing NTT execs, Setu Kulkarni and Bruce Snell, at the 2021 Black Hat Conference. Permission to use from NTT.
NTT also shares their intel, giving back to the community. For example, the Security Division publishes its threat landscape findings in monthly threat reports and the annual Global Threat Intelligence Report. The August report looks at how in the last few years, ransomware has held a steady 3-4% rate of all detected malware, according to NTT’s Global Threat Intelligence Report. But in 2020, this increased to about 6% (a nearly 50% increase). Since then, ransomware activity has increased exponentially in 2021. If we continue to see this rate of incident occurrence, we can expect ransomware to be at 12% of all detected malware before the end of 2021. This may not seem like a significant statistic, but it represents millions of detections and could indicate a total increase of about 300% in the last two years or even as much as one attack every 11 seconds.
The AppSec team does something similar in their AppSec Stats Flash Report, which are monthly state of application security updates. Furthermore, NTT contributes to CVE databases and is a member of the Cloud Security Alliance and Cyber Threat Alliance.
Read NTT’s August 2021 Threat Report here.
OneSpan
Will LaSala, Director of Security Solutions and Security Evangelist at OneSpan; Official Member of the Forbes Technology Council
OneSpan is a digital banking, security, and electronic signature company founded in 1991. Its most innovative technologies involve mobile clients, specifically application hardening. OneSpan’s Mobile Application Shielding platform can lock specific apps so that the phone will work even if one app gets hacked. Furthermore, the platform allows clients to analyze mobile devices and corresponding servers simultaneously. OneSpan’s central goal is to ensure that clients’ employees can detect and harden insecure applications and devices.

Permission to use from OneSpan.
OneSpan also contributes to the open-source community. OneSpan uses its contributions to multiple crypto libraries to receive feedback and promote transparency. In LaSala’s words, “We value the open-source communities’ support for security and feedback purposes. Releasing code to the public also protects the security community against hijacked open-source libraries.” Overall, OneSpan’s contributions to one-time password and cryptography projects exemplify its dedication to security and communal growth.
Learn more by reading OneSpan’s Global Financial Regulations Report and listening to the UserFriendly 2.0 podcast, episode Black Hat 2021 and Rodeo.
Qualys
Sumdeth Thakar, CEO of Qualys
Qualys is a software as a service company founded in 1999; it offers cloud-based security solutions in the fragmented security industry. The company has strategic partnerships with leading cloud providers, managed services providers, and consulting firms like Amazon, Microsoft, Google, Accenture, IBM, Infosys, NTT, and Verizon.

Used with permission from Qualys.
Qualys’ innovativeness stems from its ability to make security efficient, cost-effective, and scalable, offering solutions for almost every security concern. Qualys provides a one-stop solution, consolidating pre-existing technologies into a simple and easy-to-use platform.
Qualys built its backend and highly scalable platform by leveraging OSS and in-house technology. Furthermore, Qualys uses OSS to improve security event monitoring by tracking 2.5+ billion messages on Kafta and 8 trillion data points on Elastic search daily. In Thakar’s words, “You can leverage open-source technology to build massive-scale platforms; Qualys is a great example of that. As a result, we are continually increasing our public contributions, especially in the OSS community.”
Learn more: Qualys at Black Hat USA 2021
Judging Criteria
Sailing is similar to cybersecurity in that social, technical, and economic barriers often prevent beginners from joining. However, some companies and leaders strive to alleviate these barriers.
For example, Clark Mills and Major Clifford McKay created the Optimist Dinghy (Opti) to ease financial and age barriers to sailing (The Optimist Dinghy 1947-2007, 2013). The Opti design was so successful that it became one of the most popular sailboats globally and has introduced millions to sailing.
Similar to Mills and McKay’s progress in sailing, the companies recognized by the Optis Series have significantly improved their community and industry. The Optis Series highlights cybersecurity companies’ innovation and ability to address social, technical, and economic barriers. Furthermore, the definition of an optimist, “a person who is inclined to be hopeful and to expect good outcomes,” represents the outlook of cybersecurity if these trends continue (Merriam-Webster, 2021).
Here are the judging criteria:
- Highly differentiated and innovative by offering a unique product, technology, or technique.
- Demonstrates company growth, ideally supported by numerical data like funding and sponsorship, acquisitions, and hiring trends.
- Active external enthusiasm and press.
- Practices embodied by “Security Through Community,” such as inclusion initiatives and a supportive company culture.
- Socially conscious contributions that are easily proved or demonstrated (i.e., open-source code, publications, blogs, events, and licensing choices).
Bronze companies fit into one or two categories, while silver companies demonstrated three or four; gold companies exemplified all five. All companies, however, epitomized their awarded categories enough to deserve substantial recognition for their efforts.
I was very flexible with my interviews, and I did my best to create a holistic picture of each companies’ values and technologies. I also cited evidence whenever possible through public numerical data, blog posts, reports, publications, and product demos. Read the full criteria here.
About the Author
 Olivia Gallucci is a Cybersecurity Reporter for Cyber Defense Magazine and the winner of CDM’s 2021 Women in Cybersecurity scholarship. She is studying Computing Security and Computer Science at Rochester Institute of Technology.
Olivia Gallucci is a Cybersecurity Reporter for Cyber Defense Magazine and the winner of CDM’s 2021 Women in Cybersecurity scholarship. She is studying Computing Security and Computer Science at Rochester Institute of Technology.
She is a Free and Open Source Software advocate and Linux enthusiast. Olivia can be reached online here at CDM and at https://oliviagallucci.com/ and @ivyhac and https://www.linkedin.com/in/olivia-gallucci/

