- The best anti-Prime Day deals 2025 from Best Buy, Walmart, & more: Top sales from Amazon's competition
- I've tested dozens of wearables and the Apple Watch 10 is one of my favorites - here's why
- Paddle Pays $5m to Settle Tech Support Scam Allegations
- Sony is giving away free 65-inch 4K TVs right now - here's how to qualify for the deal
- Continuous Threat Exposure Management (CTEM): The Future of Vulnerability Assessment
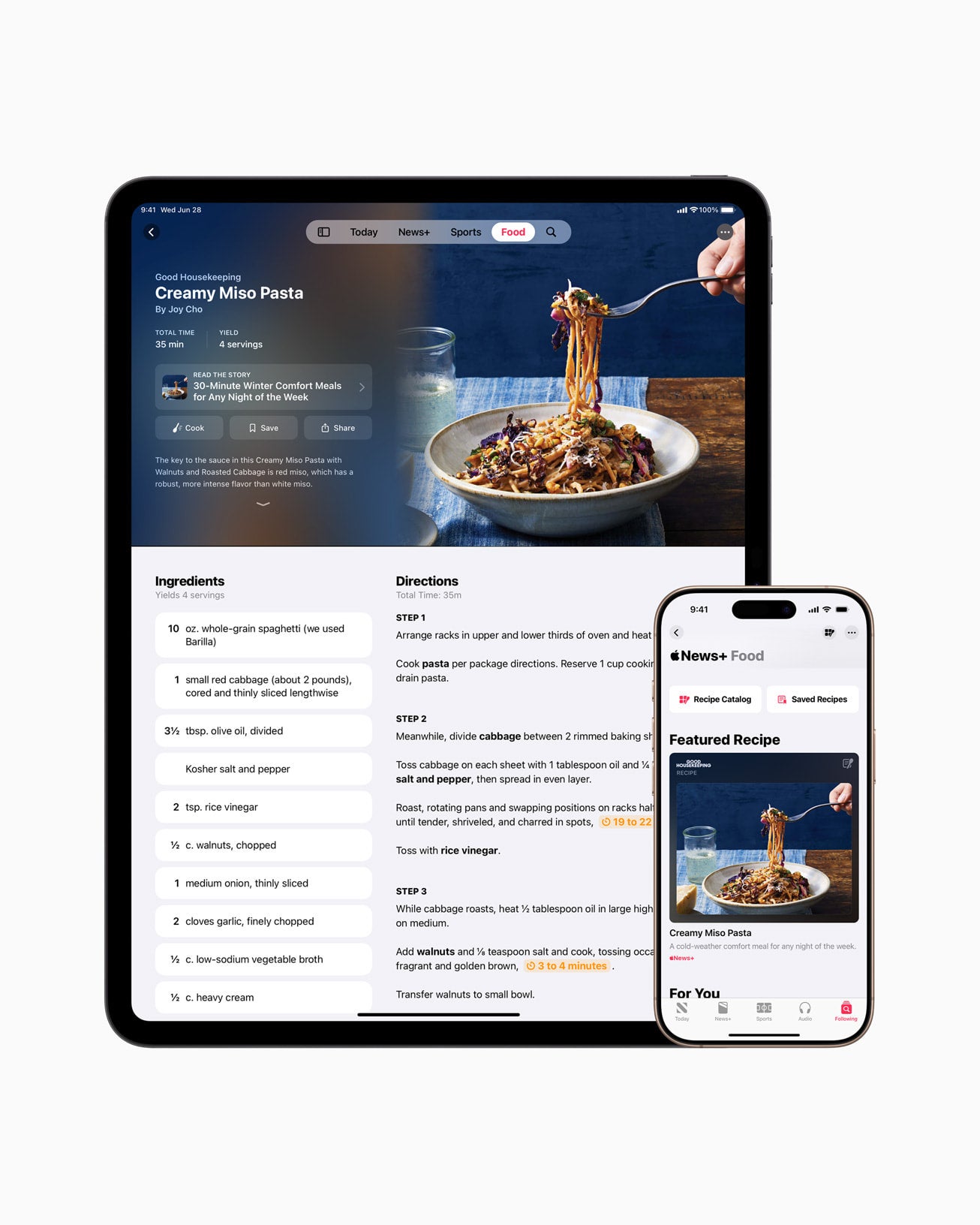
Apple Rolls Out iOS 18.4 With New Languages, Emojis & Apple Intelligence in the EU
Photo of Apple News+ Food feed. Image: Apple Apple has deployed iOS 18.4 to all compatible iPhones. The software update adds support for eight new languages on Apple Intelligence, recipes to Apple News+, and seven new emojis. Users in the European Union can also set their default navigation app other than Apple Maps. You should be prompted about the update automatically, but if not, you can initiate the download manually by going to Settings, General,…
Read More