- Select Prime members can get Kindle Unlimited for 3 months at no cost - here's how
- Modernization means putting developers in the driver’s seat
- Get a free iPhone 16 Pro for free from T-Mobile, no trade in required - here's how
- The LG C4 OLED for $800 off is one of the best Prime Day TV deals right now
- Prime members can save $10 on any $20 or more Grubhub+ order for a limited time - here's how
Billions of Devices at Risk of Hacking Due to Hidden Commands
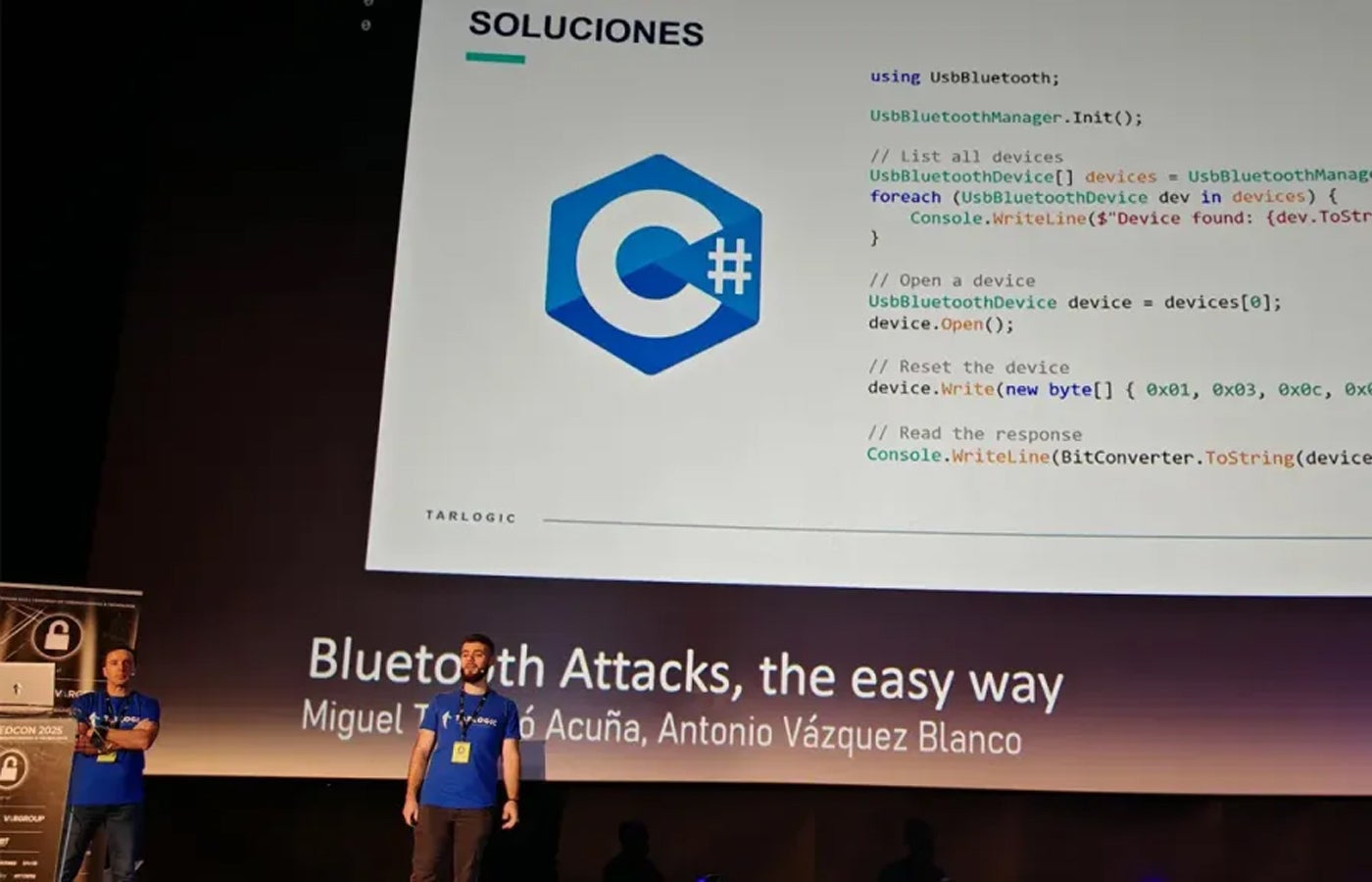
Tarlogic team giving their presentation during RootedCON. Image: Tarlogic Billions of devices worldwide rely on a widely used Bluetooth-Wi-Fi chip that contains undocumented “hidden commands.” Researchers warn these commands could be exploited to manipulate memory, impersonate devices, and bypass security controls. ESP32, manufactured by a Chinese company called Espressif, is a microcontroller that enables Bluetooth and Wi-Fi connections in numerous smart devices, including smartphones, laptops, smart locks, and medical equipment. Its popularity is partly due…
Read More