4 IoT Trends U.K. Businesses Should Watch in 2024
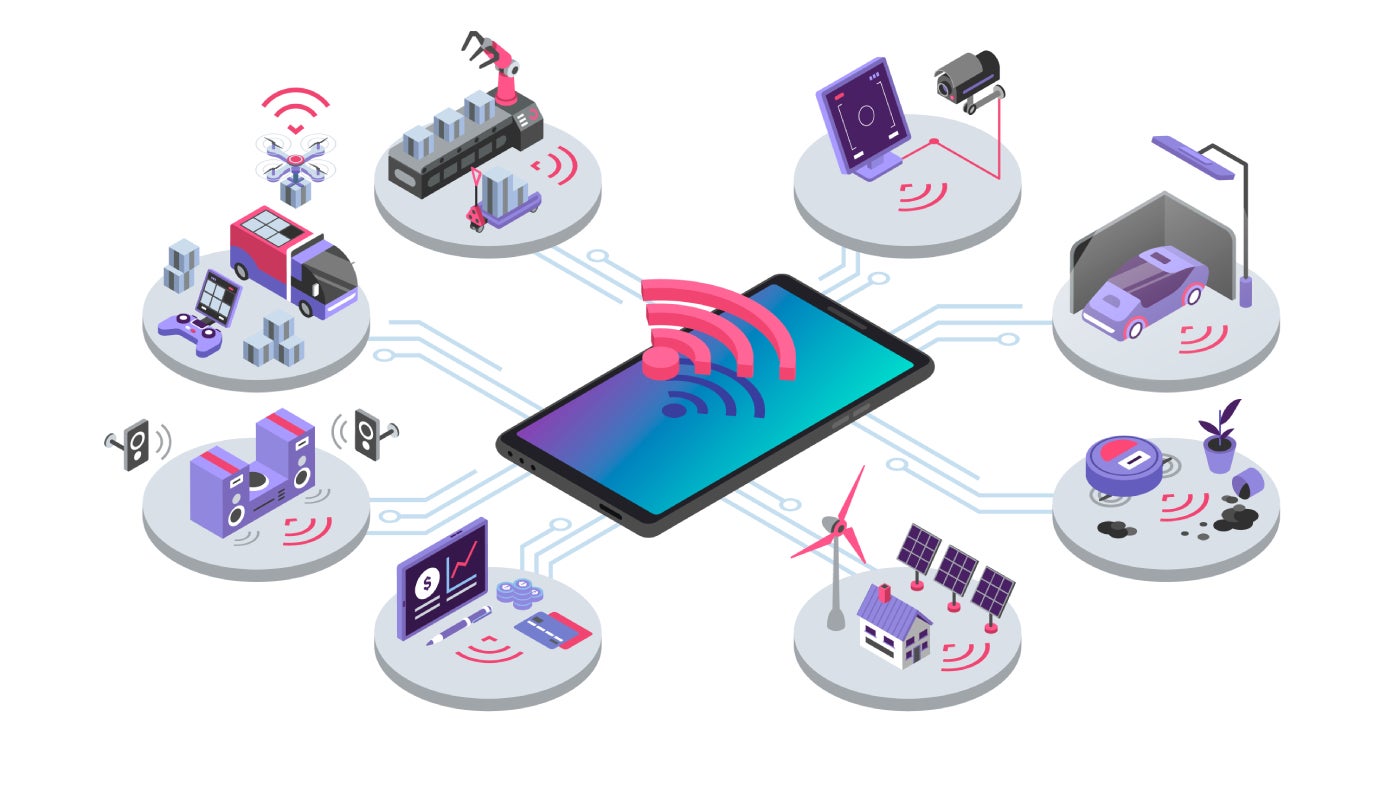
The realm of the Internet of Things encompasses more than just the latest products. As the network of connected devices grows — the number worldwide is expected to reach over 29 billion in 2027 — so do the policies, responsibilities and innovations that surround it, all of which contribute to successful IoT integration. With help from Steve Statler, the chief marketing officer at IoT technology provider Wiliot, TechRepublic has identified the top four trends emerging…
Read More