- The Growing Threat of AI-powered Cyberattacks in 2025
- I test tablets for a living and this is the Samsung tablet I recommend the most
- The Cost of Ignoring Patches: How State and Local Governments Can Mitigate Damaging Security Breaches
- I turned this 98-inch TV into an immersive at-home theater system (and it's $1,500 off)
- You can save $30 on the Apple Pencil Pro right now
Billions of Devices at Risk of Hacking Due to Hidden Commands
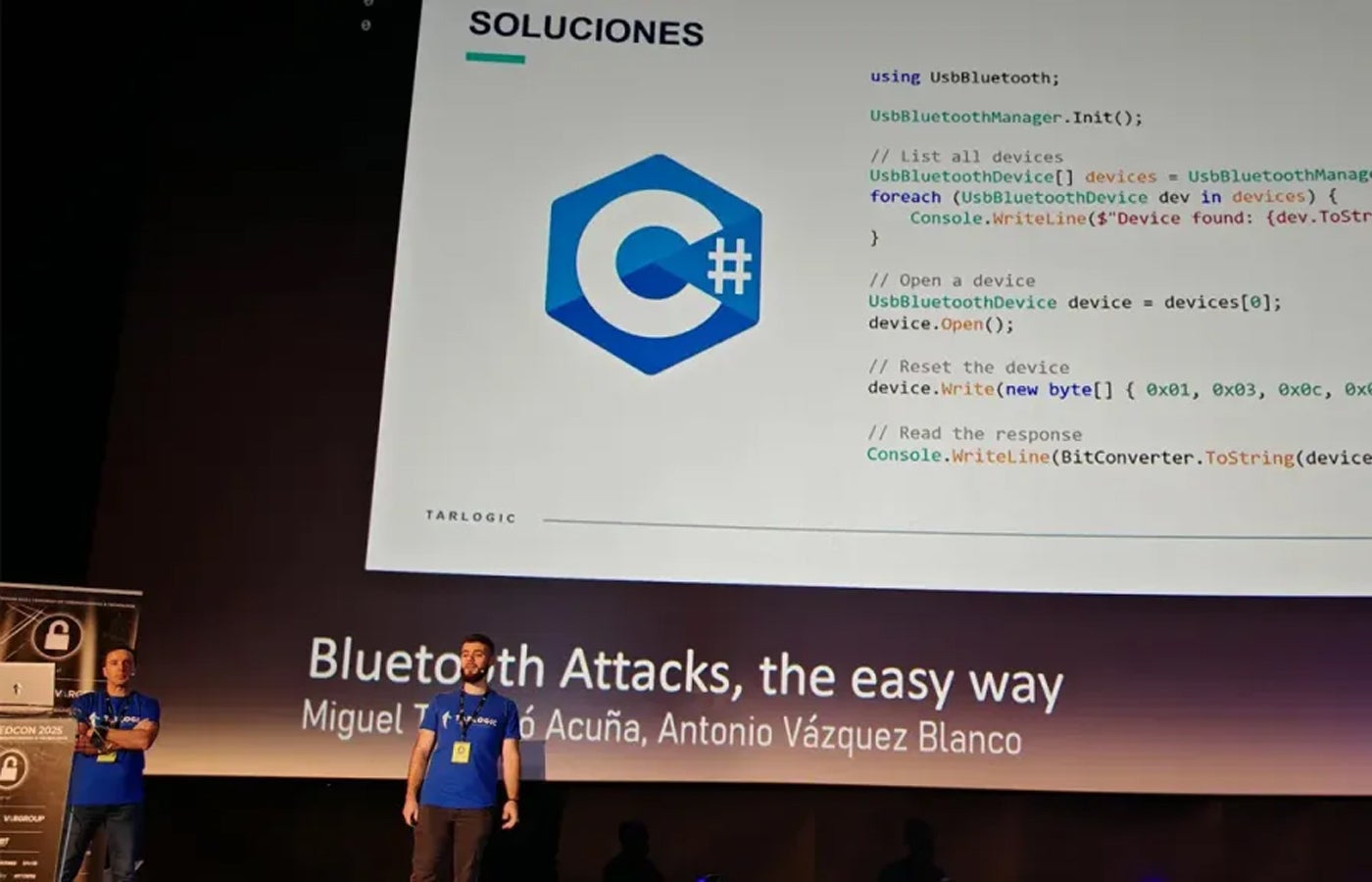
Tarlogic team giving their presentation during RootedCON. Image: Tarlogic Billions of devices worldwide rely on a widely used Bluetooth-Wi-Fi chip that contains undocumented “hidden commands.” Researchers warn these commands could be exploited to manipulate memory, impersonate devices, and bypass security controls. ESP32, manufactured by a Chinese company called Espressif, is a microcontroller that enables Bluetooth and Wi-Fi connections in numerous smart devices, including smartphones, laptops, smart locks, and medical equipment. Its popularity is partly due…
Read More